- Back to Home »
- Hacker News »
- Security vulnerability found in Cyberoam DPI devices (CVE-2012-3372)
Posted by : Anonymous
Friday, July 6, 2012
Last week, a user in Jordan reported seeing a fake certificate for torproject.org. The user did not report any errors when browsing to sites such as Gmail, Facebook, and Twitter, which suggests that this was a targeted attack. The certificate was issued by a company called Cyberoam. We first believed that this incident was similar to that of Comodo and DigiNotar, and that Cyberoam had been tricked to issue a fake certificate for our website.
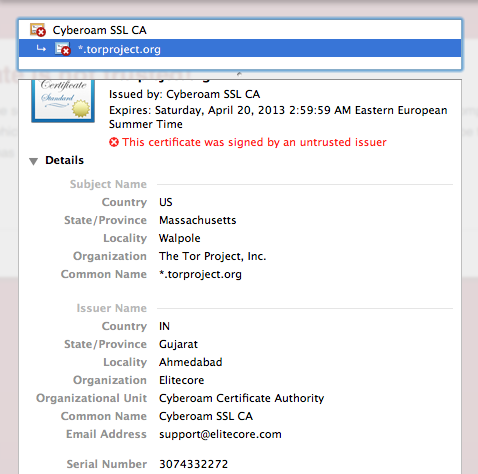
After a bit of research, we learned that Cyberoam make a range of devices used for Deep Packet Inspection (DPI). The user was not just seeing a fake certificate for torproject.org, his connection was actually being intercepted by one of their devices. While investigating this further, Ben Laurie and I found a security vulnerability affecting all Cyberoam DPI devices.
Examination of a certificate chain generated by a Cyberoam DPI device shows that all such devices share the same CA certificate and hence the same private key. It is therefore possible to intercept traffic from any victim of a Cyberoam device with any other Cyberoam device - or to extract the key from the device and import it into other DPI devices, and use those for interception.
Ben and I wrote a security advisory and notified Cyberoam of this vulnerability at 17:00 UTC on Saturday, June 30. We made it clear that we intended to publish this blog post and the security advisory on Tuesday, July 3, and encouraged them to respond promptly if they had any comments. At the same time, we notified browser vendors and asked that they blacklist the Cyberoam CA certificate in their browsers.
Cyberoam have not yet commented on this issue, apart from acknowledging our first email and saying that they are looking into it. The Cyberoam CA certificate is not trusted, and so browsers will show users a warning (unless someone has already installed the certificate). Users with the Tor Browser Bundle are not affected.
Originally Blogged at: https://blog.torproject.org/blog/security-vulnerability-found-cyberoam-dpi-devices-cve-2012-3372















Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whats app, Facebook, Instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : onlineghosthacker247@gmail.com