Archive for 2013
The Best Keyloggers Of 2013 & 2014
Keyloggers have come a long way since the days of simply recording keystrokes, and are now more commonly known as computer monitoring applications. As the years roll by, these programs become more and more powerful, recording things like websites visited, the passwords entered into these websites, and any emails sent or received. They can also emails the reports and logs, meaning we don't have to log back into the target computer. All of this combined, along with a ton of other features, make keyloggers a great tool for anyone trying to hack certain accounts.
2013 has been a good year for keylogger programs, making 2014 look extremely promising as well. The past months have seen improvements in stealth, in functionality, and in ease of use, making a keylogger as useful as ever. I've put together a quick list of keyloggers to look out for over the next few months, that are really standing out from the crowd at the moment. Let's take a look at some of the best keyloggers of 2013 and 2014:
Probably one of the best value for money keyloggers on the market. Gecko Monitor balances solid, reliable features with brilliant ease of use. The timeline feature makes this application stand out for anyone wanting a simple, easy to use way of keeping tabs on a family or office computer.
This is still one of the most popular commercial keyloggers available online. SpyAgent is a brilliant product with a lot of great features. Behaviour reports via email, graphical activity reports and the spyware detector disabler are a few of the features that make this application stand out from the crowd.
If you're looking for something a little more technical, Win-Spy may be up your street. Although this product is probably slightly harder to use, the extra features will make you feel like a real spy! With Win-Spy you can record webcam and microphone activity, so you'll get more of a feel for what's going on in the room the computer is based in. a brilliant product.
Each of the above keyloggers has their own drawbacks and benefits. Spytech SpyAgent is great if you want something that's very user friendly. Gecko Monitor is great if you want an all-rounder that is reliable. And Win-Spy is great if you want something with a lot more technical features. From a hacking point of view, all of these applications are great for doing something like uncovering a password, or monitoring incoming and outgoing emails.
Cradits : Lewis Waller
Cradits : Lewis Waller
The Future of Computers.
I have some ideas how the computer industry will be in next half-a-century, its very difficult to predict anything with vertinity now a days, especially with such advances in technology. Every five years something comes and amaze everyone. Actually thats how it works.... Something new comes in the industry and it owns it. I remember the touch sensitive mobiles were a new thing in 2005 and within half decade the whole scenario is changed, the mobile mogul Nokia is not where found in industry and everyone owns a touch mobile.
Still I would like to share my ideas, how the future will be...
Well one thing I am certain about the PC will be dead. Personal computer is now a secondary device but I see this would be finished in next 50 years. How would it happen? Well the answer is in front of us... Cloud Computing..
The Cloud Computing concept is that instead of a CPU in front of you, there is a very high speed computer somewhere in the world acting as CPU for you. Here the input is entered from your side and that info is sent to the Cloud Computer that process the info and sent the output back to you. This would be perfect as It could save alot of money, as you won't have to buy expensive computer for heavy task like gaming. And within next 2-3 decades the Quantum Computers will be reality that will increase the current chips power by million times.
But the biggest problem in this concept is availability of high speed internet as a large amount of data has to be transferred in very small amount of time, but the good news is that the technology exist at this moment and in time it will be in everyone's reach. The technology used fiber-optics and the good news is Google has already taken initiative with Google Fiber, the chance it before long the whole world will be covered with this and Cloud Computing could become a reality for everyone.
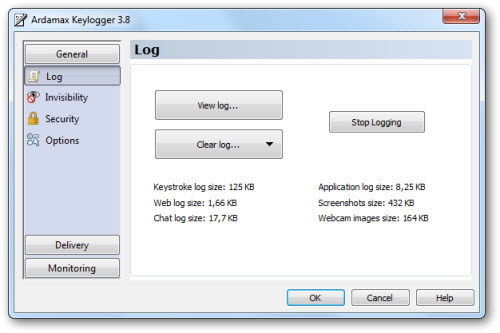
Hack Facebook With Latest Ardamax Keylogger 4.0.1
Ardamax Keylogger 4.0.1
Ardamax Keylogger is a keystroke recorder that captures user's activity and saves it to an encrypted log file. The log file can be viewed with the powerful Log Viewer. Use this tool to find out what is happening on your computer while you are away, maintain a backup of your typed data automatically or use it to monitor your kids. Also you can use it as a monitoring device for detecting unauthorised access. Logs can be automatically sent to your e-mail address, access to the keylogger is password protected. Besides, Ardamax Keylogger logs information about the Internet addresses the user has visited.
This invisible spy application is designed for 2000, XP, 2003, Vista, 7 and Windows 8.
DOWNLOAD :
Internet Download Manager [IDM] v6.16 Build 2 + Cracked
Main Features:
• Internet Download Manager supports all popular browsers including IE, AOL, MSN, Opera, Firefox, Avant Browser, and it can be integrated into any Internet application to take over downloads using unique “Advanced Browser Integration” feature. • Dynamic Segmentation and Performance.
• Easy downloading with one click. When you click on a download link in a browser, IDM will take over the download and accelerate it. IDM supports HTTP, FTP, HTTPS and MMS protocols.
• Download Speed Acceleration. IDM can accelerate downloads by up to 5 times due to its intelligent dynamic file segmentation technology.
• Download Resume. IDM will resume unfinished download from the place where they left off.
• YouTube grabber. IDM can grab FLV videos from popular sites like YouTube, MySpaceTV, and Google Video.
• Drag and Drop. You may simply drag and drop links to IDM, and drag and drop downloaded files out of Internet Download Manager.
• Automatic Antivirus checking. Antivirus checking makes your downloads free from viruses and trojans.
• Advanced Browser Integration. When enabled, the feature can be used to catch any download from any application.
• Built-in Scheduler. IDM can connect to the Internet at a set time, download the files you want, disconnect, or shut down your computer when it’s done.
• IDM includes web site spider and grabber. IDM downloads all required files that are specified with filters from web sites, for example all pictures from a web site, or subsets of web sites, or complete web sites for offline browsing. It’s possible to schedule multiple grabber projects to run them once at a specified time, stop them at a specified time, or run periodically to synchronize changes.
• IDM supports many types of proxy servers. For example, IDM works with Microsoft ISA, and FTP proxy servers.
• IDM supports main authentication protocols: Basic, Negotiate, NTLM, and Keberos. Thus IDM can access many Internet and proxy servers using login name and password.
• Download All feature. IDM can add all downloads linked to the current page. It’s easy to download multiple files with this feature.
• Download Categories. IDM can be used to organize downloads automatically using defined download categories.
• Download limits. Progressive downloading with quotas feature. The feature is useful for connections that use some kind of fair access policy (or FAP) like Direcway,
http://adf.ly/QcGCJ
Internet Download Manager (IDM) v6.15 build Crack
Internet Download Manager : The fastest download accelerator
Internet Download Manager is everyone's Favourite Download Managing Software, but like all good soft wares it is not freeware so I have this crack and patch that will make your Trial Software free and it will have no 30 Days Limit!
Multilingual: English, Spanish, French, Italian, Deustch, Japanese, Portugues, etc
Compatible with: Windows 95/98/Me/2000/NT/XP/2003/Vista/Server 2008/7 (32/64-bit)
HOW TO USE IT! ::
Internet Download Manager (IDM) v6.15
1) Install idman607.exe
2) Copy the crack to the installed folder.
3) open IDM ......
4) It will ask you for the key .... copy and past the key in the zip that you have already downloaded
Download:
http://adf.ly/QYQPR (latest link)
Internet Download Manager is everyone's Favourite Download Managing Software, but like all good soft wares it is not freeware so I have this crack and patch that will make your Trial Software free and it will have no 30 Days Limit!
Multilingual: English, Spanish, French, Italian, Deustch, Japanese, Portugues, etc
Compatible with: Windows 95/98/Me/2000/NT/XP/2003/Vista/Server 2008/7 (32/64-bit)
HOW TO USE IT! ::
Internet Download Manager (IDM) v6.15
1) Install idman607.exe
2) Copy the crack to the installed folder.
3) open IDM ......
4) It will ask you for the key .... copy and past the key in the zip that you have already downloaded
Download:
http://adf.ly/QYQPR (latest link)
Infographic: Malware is Everywhere
 Infographic authored by Inspired eLearning, your source for security awareness training materials. To view the original post, click here.
Infographic authored by Inspired eLearning, your source for security awareness training materials. To view the original post, click here.
Monitoring Someones Facebook With A Keylogger
Occasionally you'll want to access the accounts of someone who's computer you have access to. You may have a reason for needing to see inside the Facebook account of someone you live with or the Hotmail account of a friend or spouse. Of course, these accounts are immune to the usual hacking methods, the easiest way to gain access is to utilise a keylogger.
If you're not familiar with keyloggers (also referred to as computer monitoring software) they're programs that run silently on the target computer logging every activity that is undertaken on that machine. You can then go back over the logs at a later date. Keyloggers are perfect for retrieving passwords to sites like Facebook and Hotmail. Once installed you let them run for a number of days or until you know the site has been accessed, then you re-open the keylogger to see what has been typed into that particular website.
Installing a keylogger on a computer is also a perfect way to monitor someones Facebook activities. The software will take screenshots at set intervals (you could set it to every few seconds or every few minutes) and will monitor every keystroke entered, meaning you could monitor chat conversations and messages as well as emails in Hotmail and other webmail clients like Gmail.
Of course all of this is done in complete stealth and setting up a keylogger is very quick and simple. You simply download the installer (or have it prepared on a flash drive) install the program in a couple of minutes and set up your secret key combination and password, which is used to access the logs, everyone else won't have a clue they're being monitored. If you only have access to the targets computer once and can't get back to check the logs you can set them to be sent remotely via email.
Keyloggers are great for the beginner hacker and some of them even have a remote install function or a compiler that creates a disguised installer package that can be sent to the target as an email. They also monitor things like documents deleted, saved, printed etc and all applications used and websites visited. If you're interested in downloading a free trial of a keylogger check out Gecko Monitor by heading to http://www.GeckoMonitor.com